The Magnet Forensics Weekly CTF has been running since October and sets one question each week using an image that changes each month. The October questions were based on an Android filesystem dump, and November’s related to a compromised Hadoop cluster built on Ubuntu Linux. The December challenges return to more familiar territory for me – Windows memory analysis!
These questions use the memory image from the Magnet Virtual Summit 2020, which I first examined during the MVS CTF earlier this year. You can find the rest of my Magnet Weekly CTF write-ups here.
The Week 11 questions were set by Lynita Hinsch and, unusually for a memory analysis challenge, I didn’t use Volatility at all this week. Instead, inspired by Kevin Pagano’s solution for Week 10, I used Bulk Extractor and Wireshark to quickly examine network activity extracted from the memory image.
Part 1 (20 points)
What is the IPv4 address that myaccount.google.com resolves to?
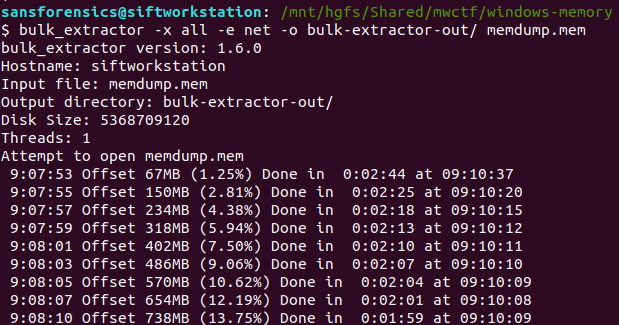
One of my favourite things about the Magnet Weekly CTF is reading write-ups from the other participants. A lot of the time we solve the challenges in the same way, but every so often I come across some technique or tool that I had no idea existed! One such technique was using Bulk Extractor to carve network activity from a memory image into a PCAP file that could then be analysed in Wireshark. I’ve used Bulk Extractor before, but had no idea it could do that!
The following command disables all of the Bulk Extractor modules (-x all), then enables the network module (-e net) and writes output to the specified directory.
bulk_extractor -x all -e net -o bulk-extractor-out/ memdump.mem
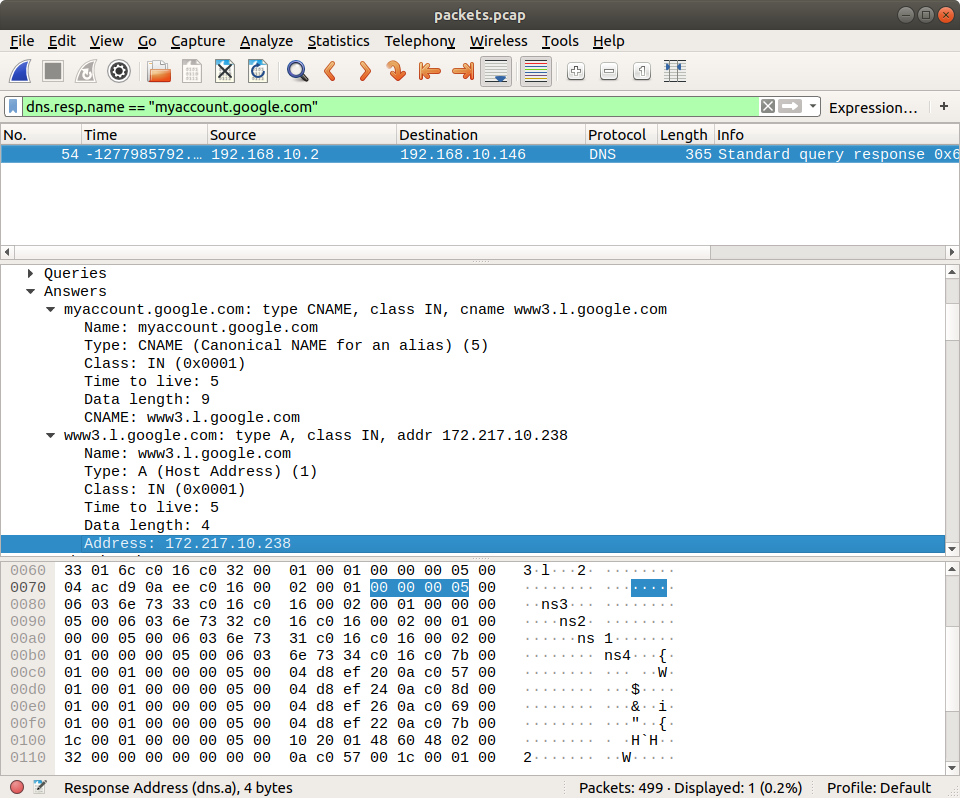
A few minutes later we have a PCAP file! From here on this is essentially a network analysis task. Opening the PCAP in Wireshark we can quickly filter the DNS responses for myaccount.google.com:
dns.resp.name == "myaccount.google.com"
In this case the initial response was a CNAME record, which led to the A record, and ultimately to the IPv4 address.
Flag (Part 1)
172.217.10.238
Part 2 (5 points)
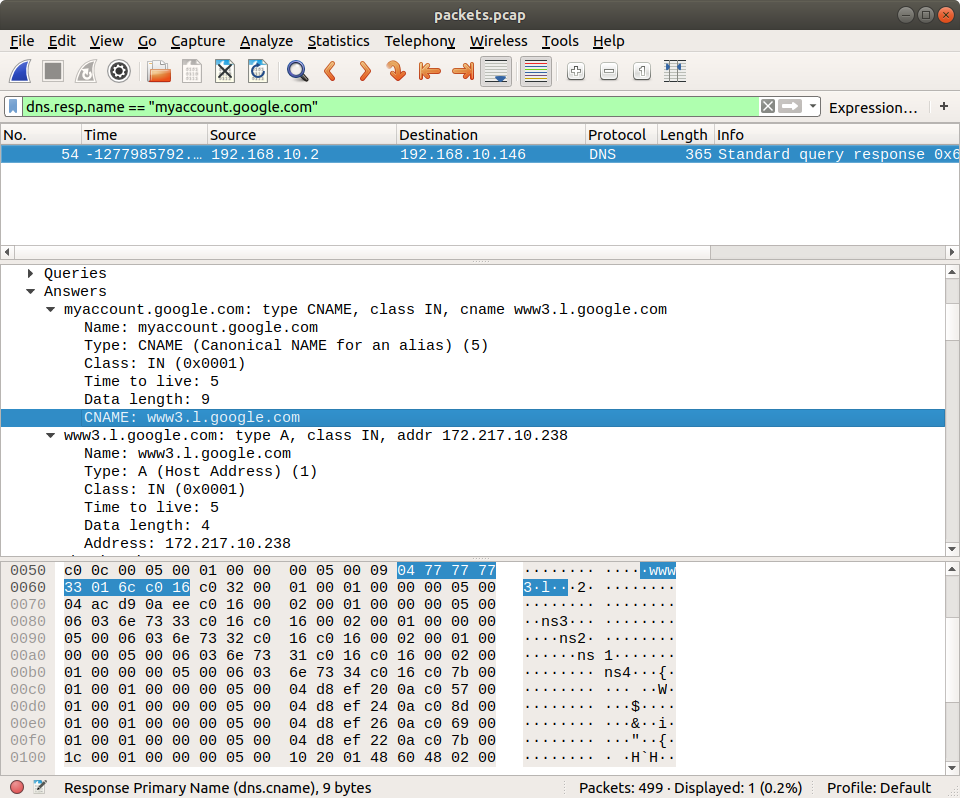
What is the canonical name (cname) associated with Part 1?
Wireshark makes this easy. The CNAME record was included in the same DNS response packet, giving us the second flag.
Flag (Part 2)
www3.l.google.com