This packet capture seems to show some suspicious traffic.
All that is provided for this challenge is a small PCAP, and the observation that it contains “some suspicious traffic”. Let’s go!
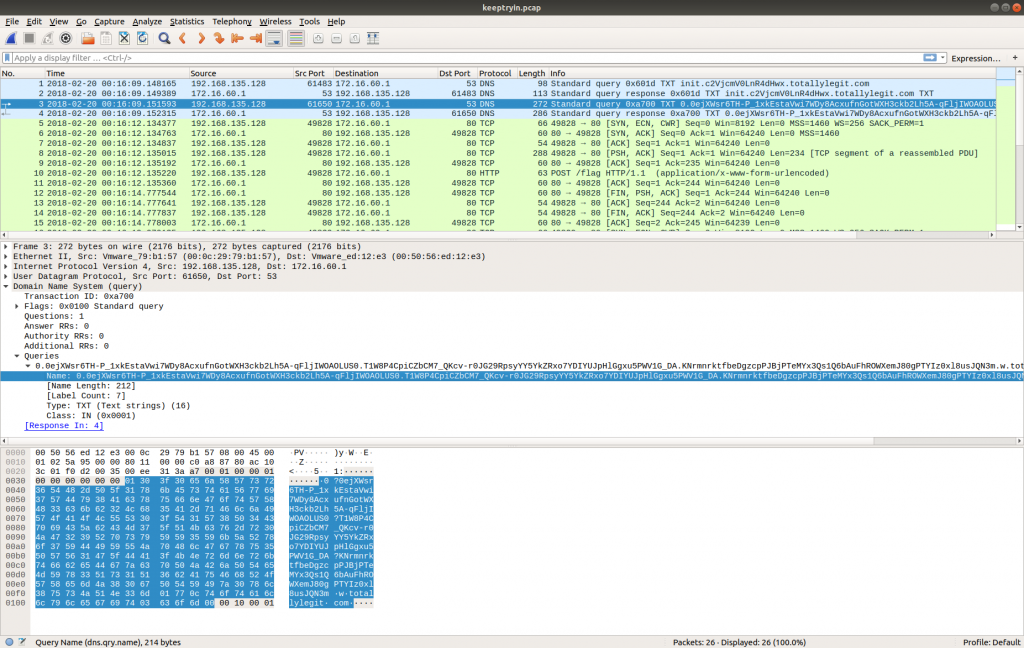
Opening the PCAP in Wireshark we find that it only contains 26 packets.
The first thing my eye was drawn to was the DNS traffic. The use of TXT records with long, seemingly random hostnames looks a lot like DNS tunnelling, but let’s see what else we have.
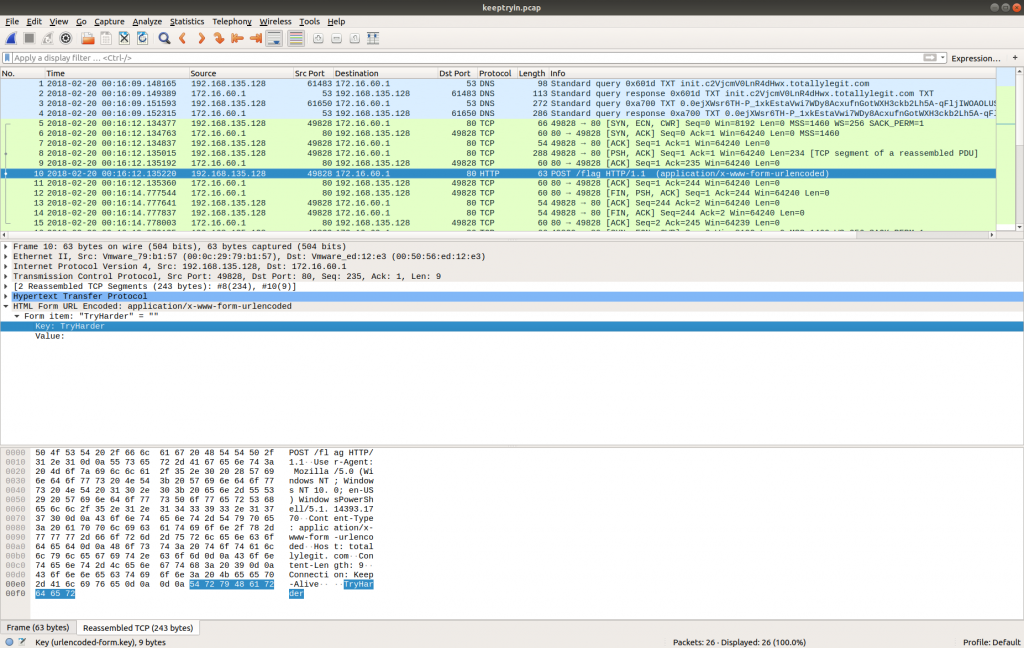
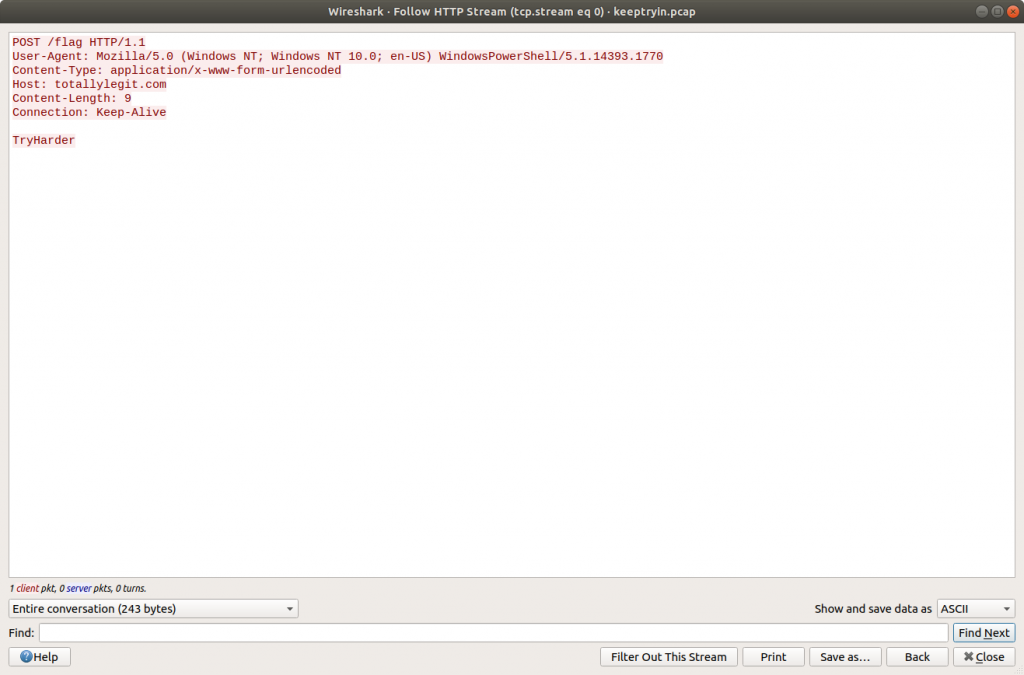
Looking through the PCAP we find that Packet 10 contains a HTTP POST request to a resource named /flag. Following the HTTP Stream (tcp.stream eq 0) shows the following text:
TryHarder
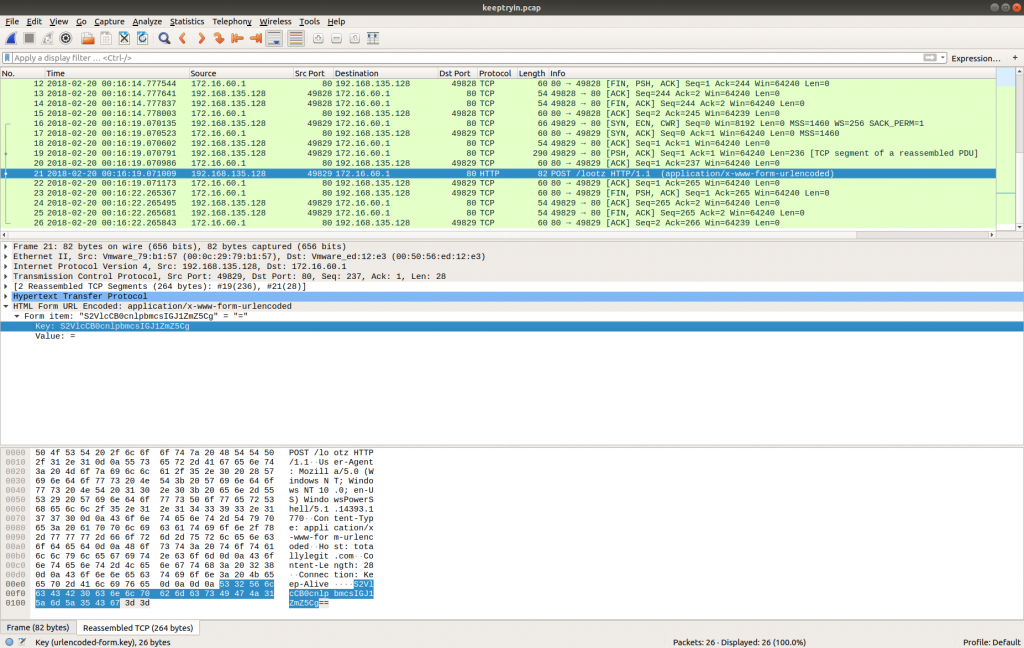
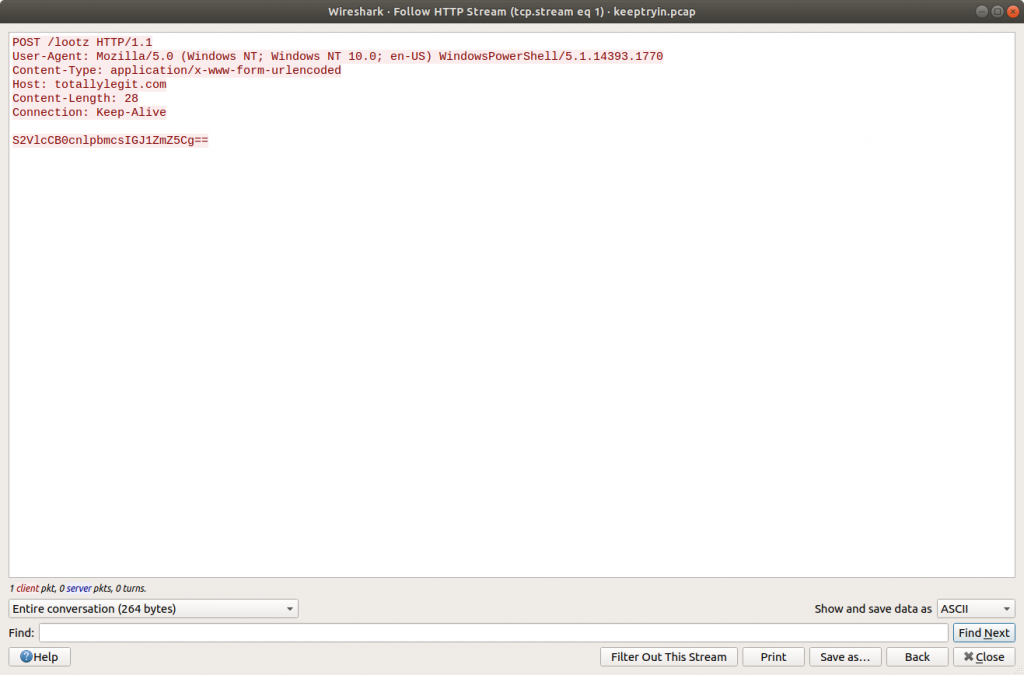
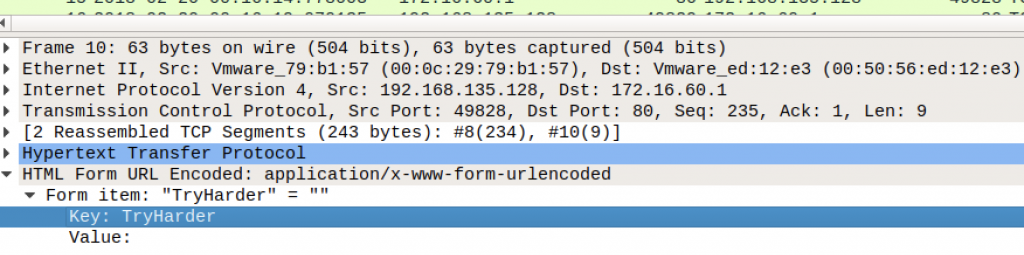
Similarly, in Packet 21 we find another HTTP POST request to a resource /lootz.
Following the HTTP Stream (tcp.stream eq 1) give us what appears to be base64 encoded text.
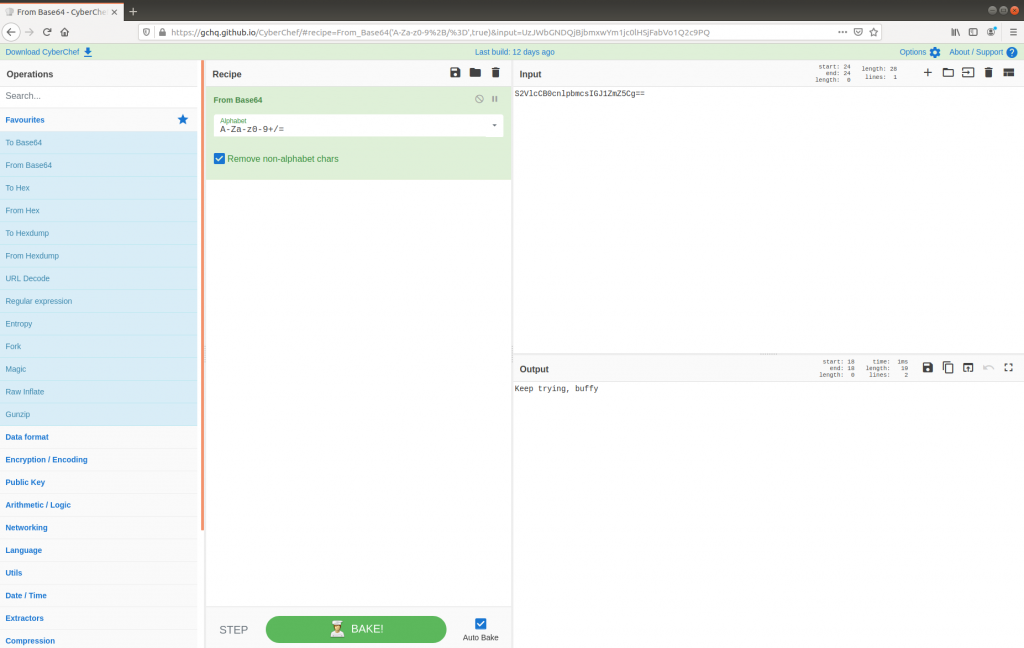
S2VlcCB0cnlpbmcsIGJ1ZmZ5Cg==
Decoding with CyberChef gives us the following:
Keep trying, buffy
Neither of these have any immediately obvious use, so let’s go back to the DNS traffic and take a closer look.
dns
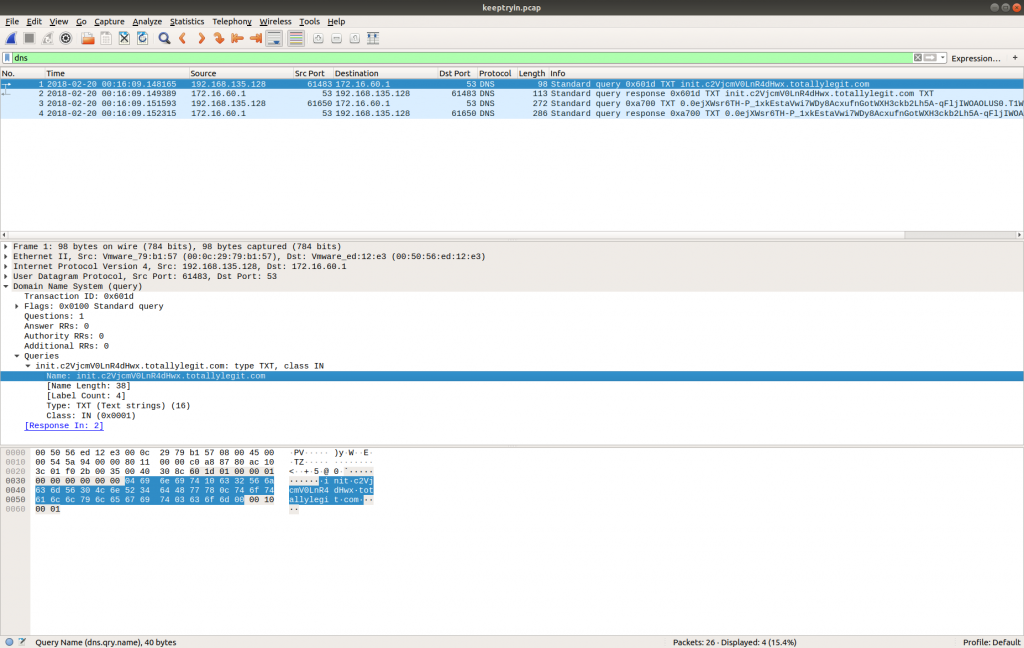
The first DNS request is for the following TXT record:
init.c2VjcmV0LnR4dHwx.totallylegit.com
We can drop the first part of the hostname (init) and the domain (totallylegit[.]com), leaving us with a seemingly random string. From the character set we could be dealing with more base64, however as the standard base64 character set is not safe for use within URLs, we will have to specify the base64url decoding instead. Fortunately CyberChef makes this trivial by offering multiple Alphabets as an option in the From Base64 operation.
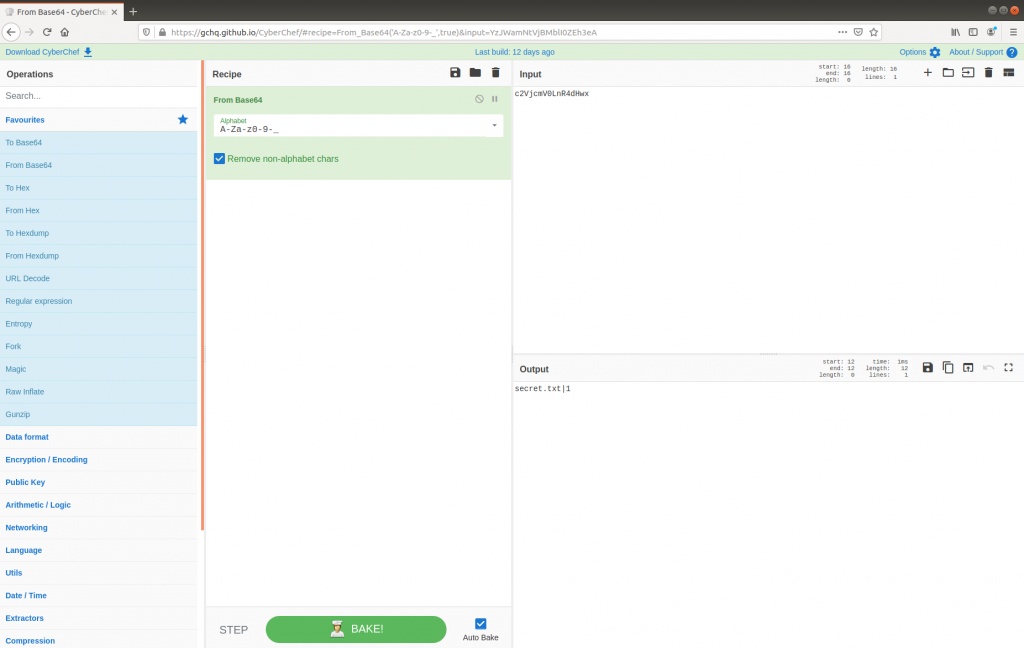
c2VjcmV0LnR4dHwx
This looks promising! The first DNS request did in fact contain base64 (strictly speaking, base64url) data, which decoded to:
secret.txt|1
The second DNS request is for the following TXT record:
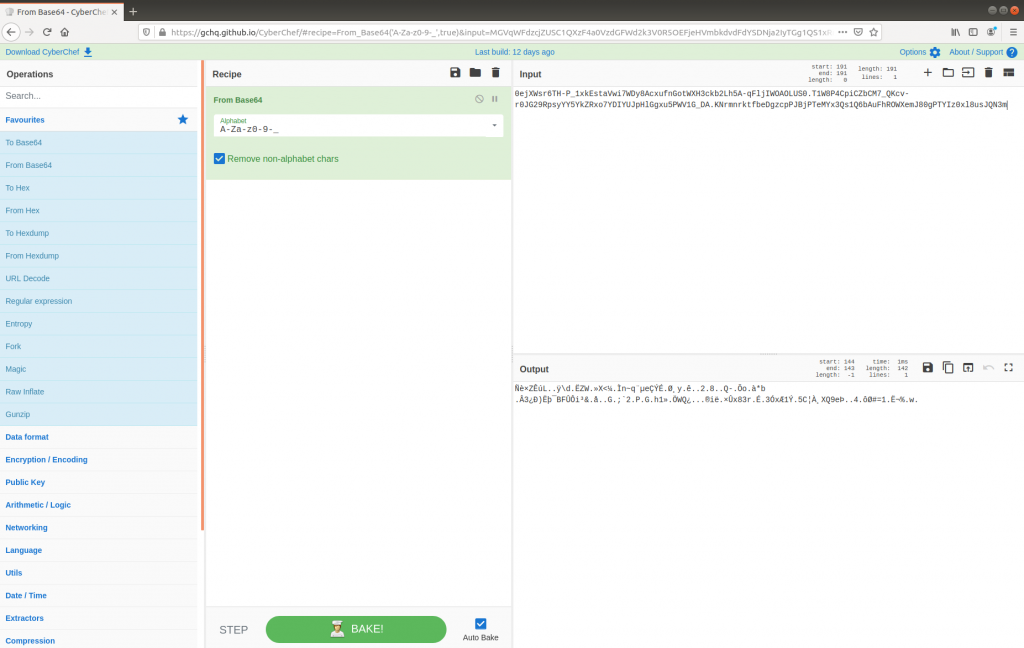
0.0ejXWsr6TH-P_1xkEstaVwi7WDy8AcxufnGotWXH3ckb2Lh5A-qFljIWOAOLUS0.T1W8P4CpiCZbCM7_QKcv-r0JG29RpsyYY5YkZRxo7YDIYUJpHlGgxu5PWV1G_DA.KNrmnrktfbeDgzcpPJBjPTeMYx3Qs1Q6bAuFhROWXemJ80gPTYIz0xl8usJQN3m.w.totallylegit.com
Again, after dropping the first, and trailing parts of the request we are left with the following base64url encoded string:
0ejXWsr6TH-P_1xkEstaVwi7WDy8AcxufnGotWXH3ckb2Lh5A-qFljIWOAOLUS0.T1W8P4CpiCZbCM7_QKcv-r0JG29RpsyYY5YkZRxo7YDIYUJpHlGgxu5PWV1G_DA.KNrmnrktfbeDgzcpPJBjPTeMYx3Qs1Q6bAuFhROWXemJ80gPTYIz0xl8usJQN3m
As before, decoding this in CyberChef with the URL Safe alphabet works, but the data appears to be corrupt…
…or encrypted. Thinking back to the first HTTP POST request in Packet 10, the form data might have been a hint.
Key: TryHarder
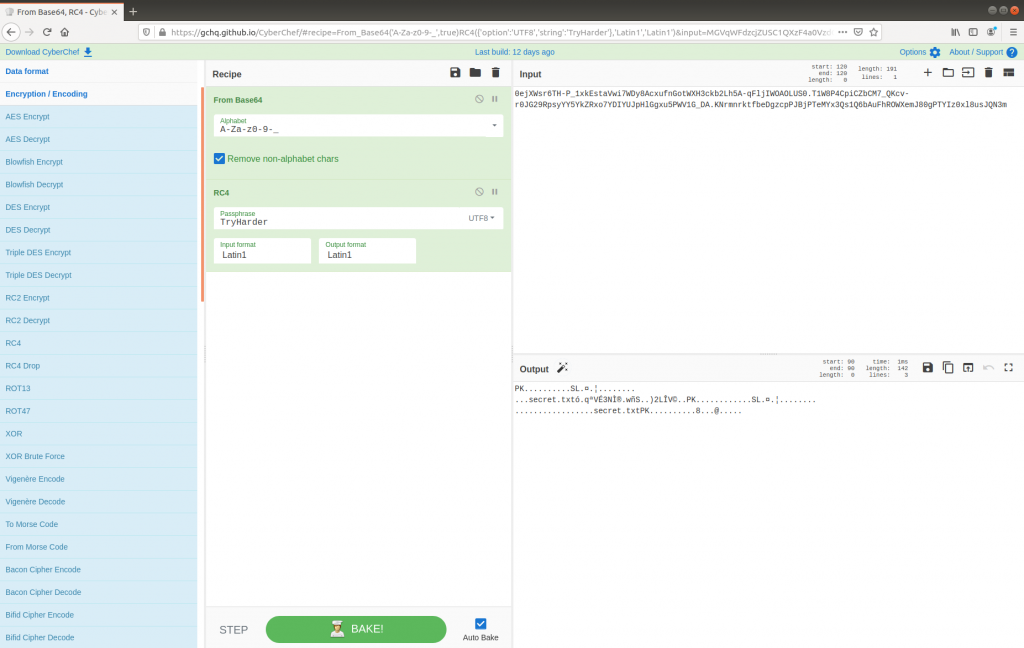
My first thought was to add an XOR operation to my CyberChef recipe, using TryHarder as the key, but no luck. Fortunately CyberChef makes it easy to try other ciphers, and not too long later I found that decrypting using RC4 with TryHarder as a key successfully produced a Zip archive containing a file named secret.txt – as per the first encoded DNS request.
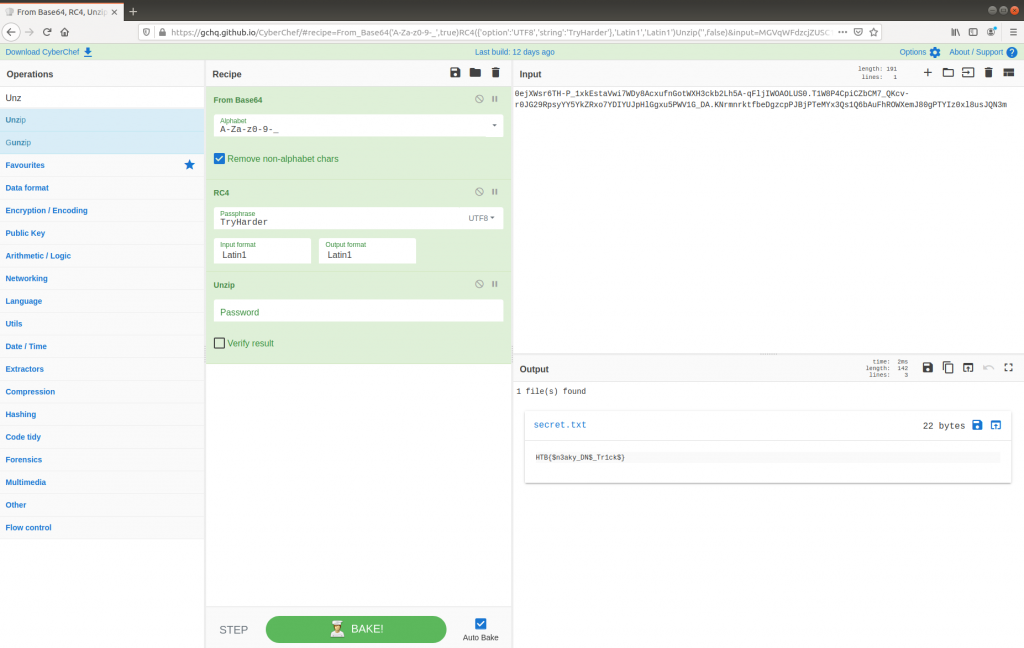
Adding the Unzip operation to the CyberChef recipe gives us our flag, and the challenge is complete.
Flag
HTB{$n3aky_DN$_Tr1ck$}