The first CTF created by Security Blue Team was initially for subscribers only, but was made available to the public for a short time at the end of February 2020. While it covered network traffic analysis, password cracking, steganography, forensics, and some general knowledge challenges I didn’t have as much time as I would have liked to spend, so concentrated on the aspects that were most interesting to me personally.
This write-up covers the first of three password cracking challenges – Weekpass. You can find the rest of my write-ups for Security Blue Team VIP CTF #1 here.
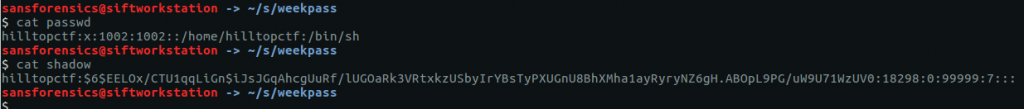
We are provided with two files – passwd and shadow – which contain the user account details and password hash. For this challenge we will combine the two files, and use John The Ripper to crack the hash.
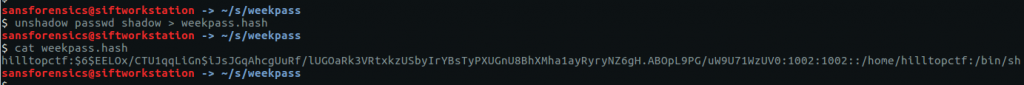
To combine the files we use a utility bundled with John called unshadow
unshadow passwd shadow > weekpass.hash cat weekpass.hash
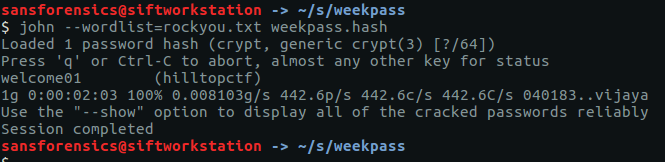
Now that we have our hash in a format that John can use, we need to find a wordlist or dictionary; the list of approximately 14.3 million plaintext passwords from the 2009 RockYou breach is still a good starting point a decade onwards. The list is included with Kali linux or can be downloaded from the internet. As I am using the SANS SIFT virtual machine, I downloaded the list and passed it to John via the following command.
john --wordlist=rockyou.txt weekpass.hash
After a couple of minutes work (a downside of cracking passwords on virtual machines) John has found a match – welcome01 – and we have our flag.
hilltopCTF{welcome01}
Next up in the password cracking category, Switching Teams.