The first CTF created by Security Blue Team was initially for subscribers only, but was made available to the public for a short time at the end of February 2020. While it covered network traffic analysis, password cracking, steganography, forensics, and some general knowledge challenges I didn’t have as much time as I would have liked to spend, so concentrated on the aspects that were most interesting to me personally.
This write-up covers the second of three password cracking challenges – Switching Teams. You can find the rest of my write-ups for Security Blue Team VIP CTF #1 here.
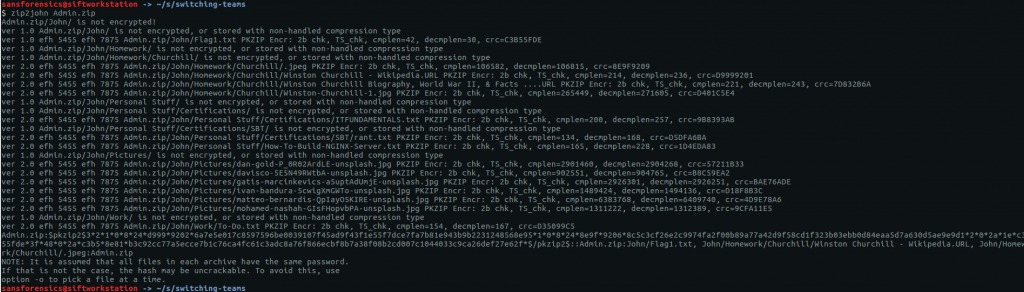
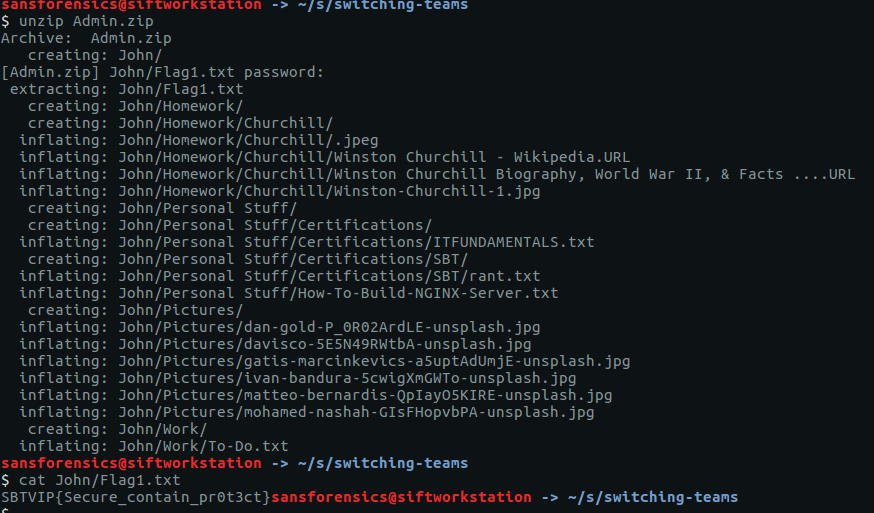
This time we have a password-protected ZIP archive name Admin.zip, and a dictionary file named SuperSecret.txt. We start by extracting the password hash from the archive using the zip2john utility.
zip2john Admin.zip
This archive contains a mix of plaintext and password-protected files. To make sure we get the correct password, we can specify which file we are interested in with the -o flag. The archive contains a file called John/Flag1.txt which sounds like something we are interested in.
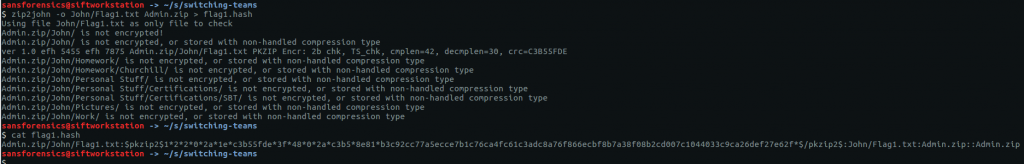
With the following command we can extract the correct password hash to a file.
zip2john -o John/Flag1.txt Admin.zip > flag1.hash cat flag1.hash
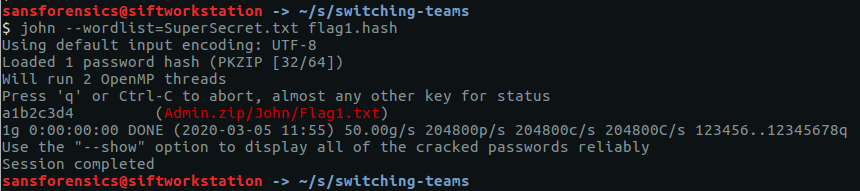
So now we have a file containing our hash, and a file containing our wordlist. We could use a brute-force attack as suggested in the question, but let’s use what we are given first. Let’s feed both files to John.
john --wordlist=SuperSecret.txt flag1.hash
Almost immediately John returns our password – a1b2c3d4 – but we’re not done yet. Our flag is inside the password-protected archive, so let’s extract it (supplying our cracked password when prompted) and take a look.
unzip Admin.zip cat John/Flag1.txt
There we go. Now we have our flag.
SBTVIP{Secure_contain_pr0t3ct}
The final password cracking challenge – Jumbled – involved setting a mask and was more suited to a different password-cracking tool, hashcat. I was unable to get hashcat to run correctly on my SIFT virtual machine, and so as I had limited time for this CTF, I decided to skip it and move on to other challenges instead.
1 thoughts on “Security Blue Team VIP CTF #1 – “Switching Teams” Write-up”