Memlabs is a set of six CTF-style memory forensics challenges released in January 2020 by @_abhiramkumar and Team bi0s. I have been working on the Magnet Weekly CTF recently so the other write-ups I had in progress have been sitting partially finished for a while now. This write-up covers Lab 5 – Black Tuesday, which I worked on back in July! You can find the rest of my Memlabs write-ups here.
MD5: 9dd6cb1134c9b018020bad44f27394db SHA1: 289ec571ca6000b6234dee20c28d4cdba13e4ab7
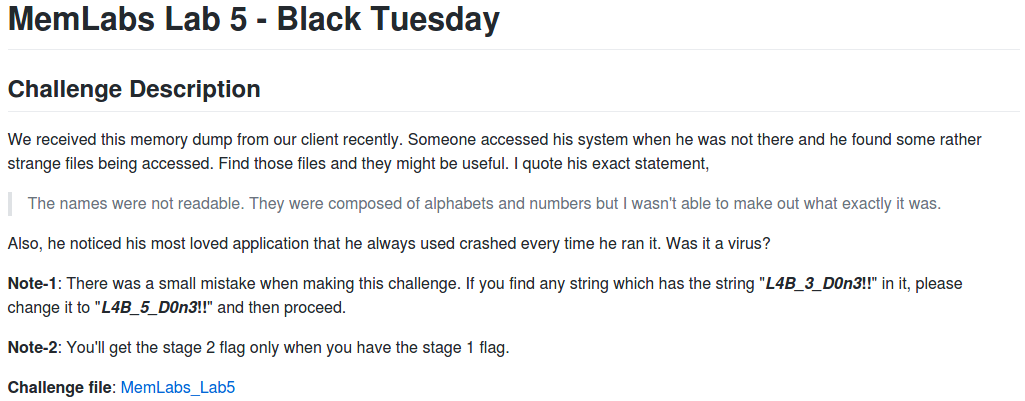
After downloading the memory image and calculating the hashes, the first thing to do is determine which profile Volatility should use for the rest of the analysis.
vol.py -f MemoryDump_Lab5.raw imageinfo
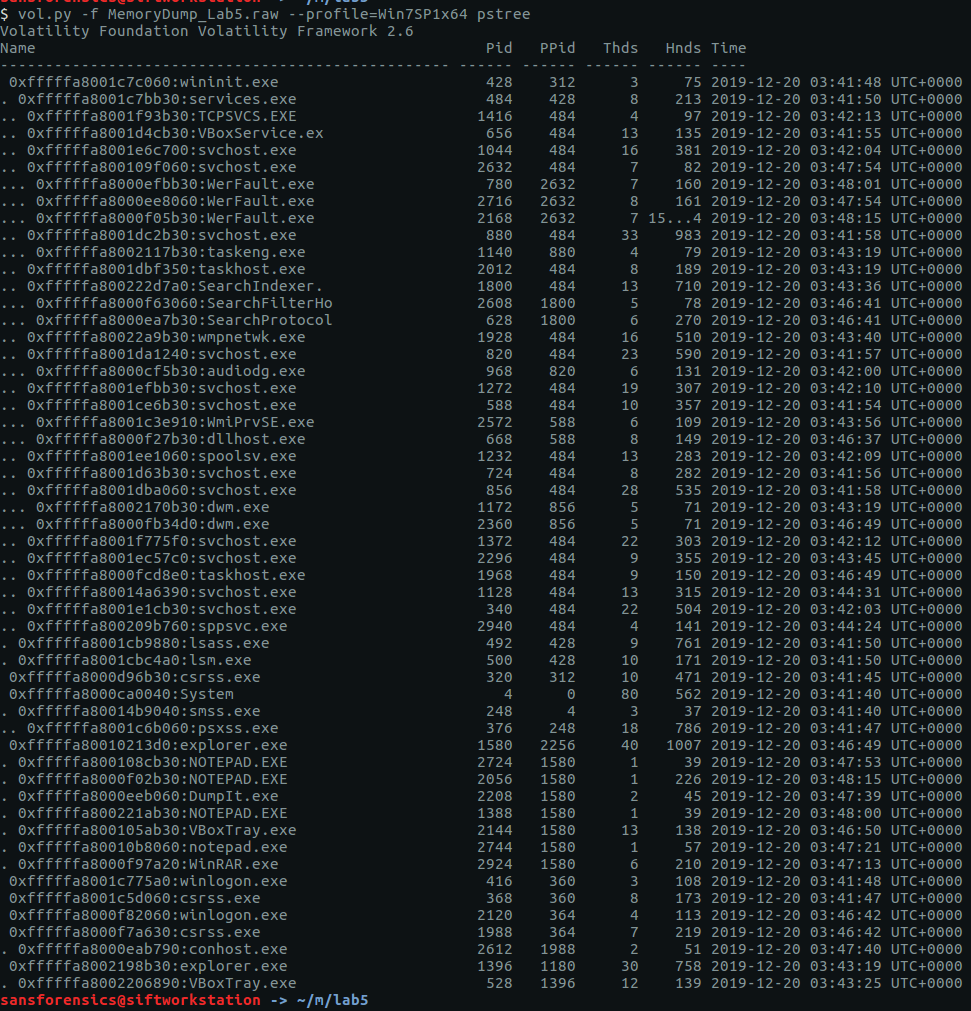
The imageinfo plugin suggests a few profiles we can use; let’s go with Win7SP1x64 for now, and check the running processes with pstree.
vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 pstree
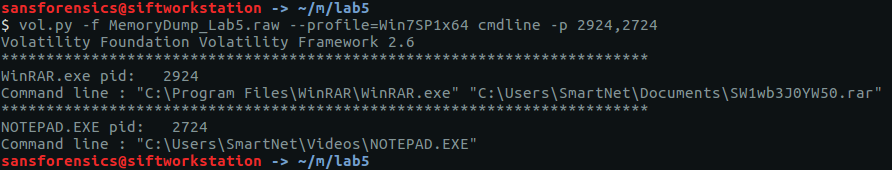
There are a few user processes that warrant investigation but no immediately obvious starting point. The cmdline plugin will display any command-line arguments that were passed when the process was started. Initially I ran the cmdline plugin with no additional arguments, but I have truncated the output to focus on two of the more interesting processes – WinRAR.exe and NOTEPAD.EXE.
vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 cmdline -p 2924,2724
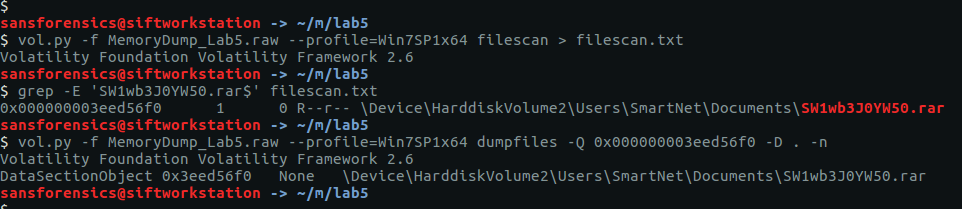
We can see that the WinRAR process has a file associated with it; using the filescan and dumpfiles plugins we can extract this file from the memory image.
vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 filescan > filescan.txt grep -E 'SW1wb3J0YW50.rar$' filescan.txt vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003eed56f0 -D . -n
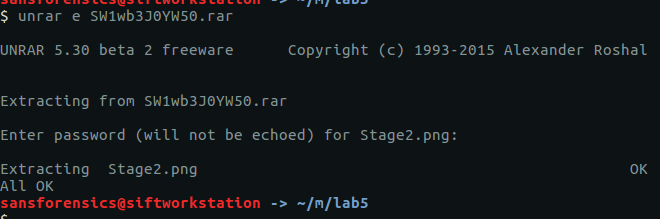
Now we have the RAR file…
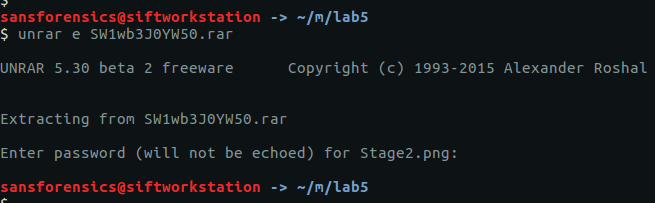
unrar e SW1wb3J0YW50.rar
…but we don’t have the password to open it. The RAR file contains Stage2.png, let’s go find the Stage 1 password.
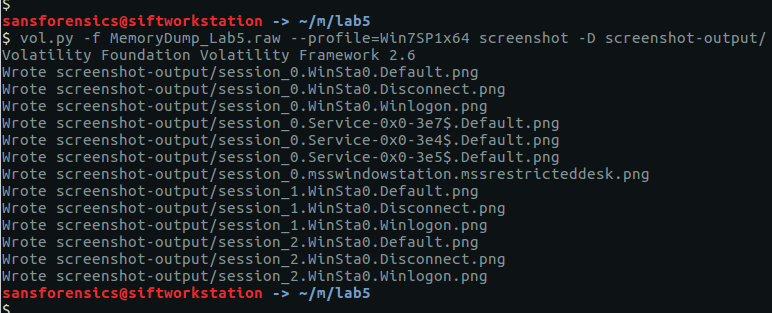
After going down a few dead ends, I tried the screenshot plugin which, as the name suggests, allows us to see what was displayed on the desktop at the time the memory dump was taken. The screenshots are actually wire-frame drawings showing the positions and titles of the displayed windows. It won’t show us the full window content, but it is often enough to get an idea of what was displayed on the desktop.
vol.py -f MemoryDump_Lab5.raw --profile=Win7SP1x64 screenshot -D screenshot-output/
The screenshot plugin outputs a number of images; most are empty but one (session_1.WinSta0.Default.png) shows us that the Windows Photo Viewer was displaying a file with what looks to be a base64 filename:
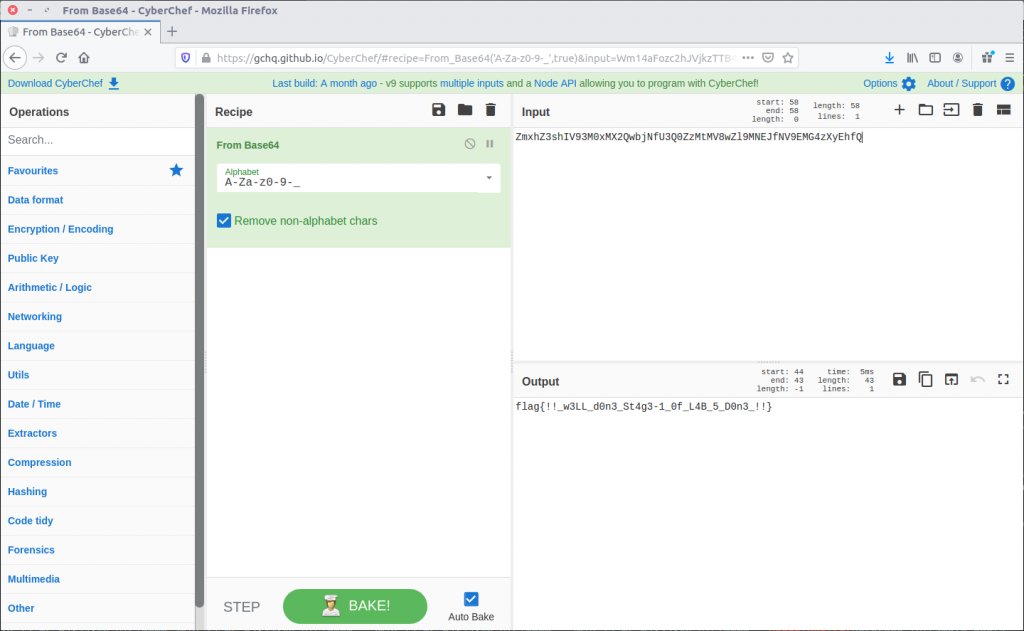
ZmxhZ3shIV93M0xMX2QwbjNfU3Q0ZzMtMV8wZl9MNEJfM19EMG4zXyEhfQ
We can decode the base64 with CyberChef…
…and there’s our Stage 1 flag:
flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5_D0n3_!!}
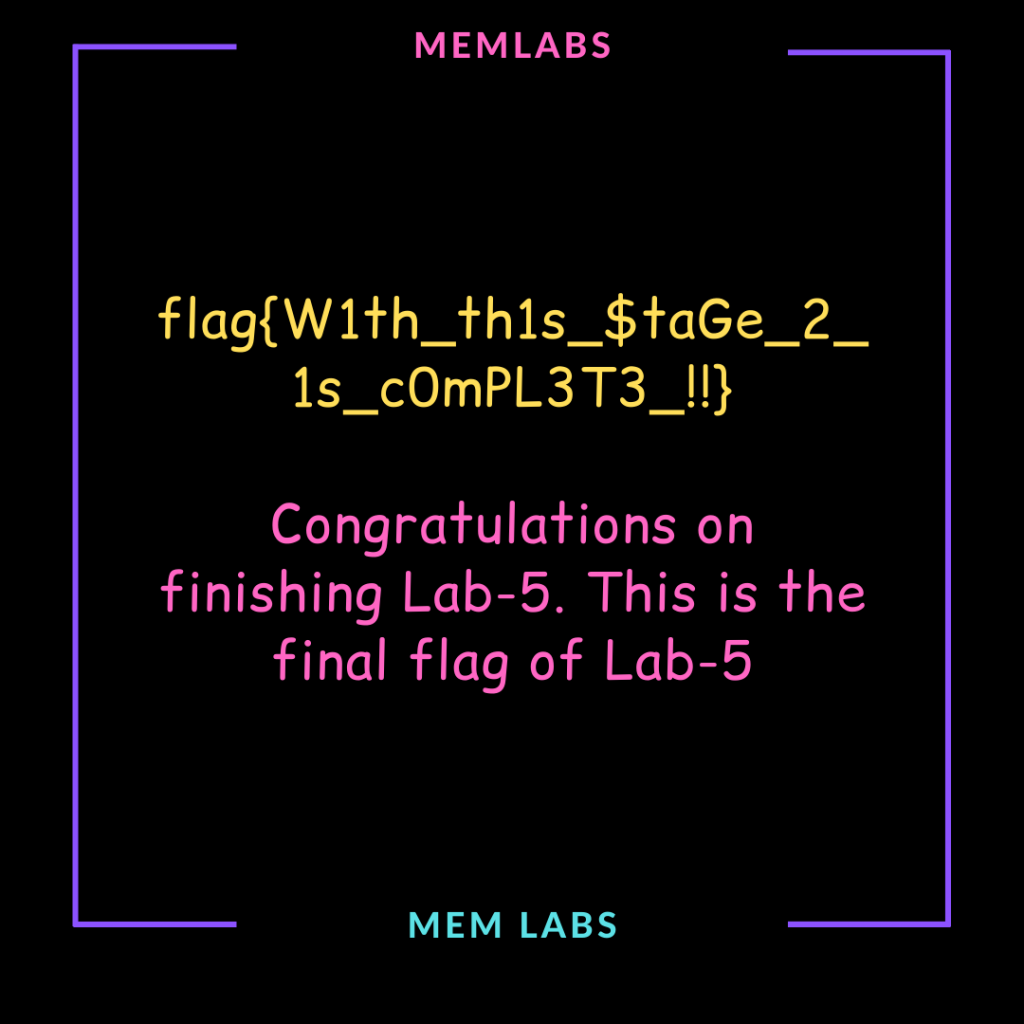
Now, we can go back to the RAR file and extract the Stage2.png:
Success!
flag{W1th_th1s_$taGe_2_1s_c0mPL3T3_!!}
Between “completing” this lab in the middle of July 2020 and finding time to write it up (in November!), the challenge description has been updated with the following note:
This challenge is composed of 3 flags. If you think 2nd flag is the end, it isn’t!! 😛
This kind of thing was exactly what put me off the Memlabs challenges in the first place. Maybe the NOTEPAD.EXE process (PID: 2724) is worth examining, but I’m moving on.


for part three: stAg3_5.txt 🙂
find a 2744 process