In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. I published my network traffic analysis write-ups earlier in the year, and after spending some more time on memory analysis, I decided to take a look at something different.
Over the last few months I have been seeing more and more chat about iLEAPP – the iOS Logs, Events, and Plists Parser – from Alexis Brignoni (with plugins and artefact definitions submitted by many others!), and wanted to set some time aside to play with it myself. I didn’t have any jailbroken iOS devices or fancy iOS acquisition kit to hand, but I remembered the iOS section of the Champlain College CTF and realised I could use that instead.
This post is nowhere near a full write-up of the iOS analysis section. Instead, think of it more as an illustration of what can be accomplished with iLEAPP and a spare hour on a Sunday afternoon! I used the CTF questions as a guide for the analysis, however if I couldn’t see a way to get the answer directly from iLEAPP I simply moved on to the next one. With that in mind, let’s go!
Installing iLEAPP (on Ubuntu 20.04 LTS)
The first thing to note is that iLEAPP requires at least Python 3.7.4 in order to run.
As far as possible, I like to use free or open-source tools when writing-up CTF challenges so that they are accessible for people without access to commercial tools. Purely out of habit I have been using an old copy of the SANS SIFT virtual machine based on Ubuntu 16.04 for most of my write-ups to this point. I recently took the time to setup a copy of the updated SIFT VM based on Ubuntu 18.04, but after fighting with multiple different versions of Python for a while, I gave up and built a new virtual machine with a default installation of Ubuntu 20.04 which (in my case, anyway) shipped with Python 3.8 and made the iLEAPP installation so much simpler!
The iLEAPP readme contains easy to follow installation instructions but does assume that Python pip is already present. I had to install pip for Python 3 using the Ubuntu apt package manager. I also had to install the git client, again, using apt.
sudo apt update && sudo install git python3-pip
Once the correct version of pip is installed the remaining steps are quite straightforward. First, clone the repository from Github:
git clone https://github.com/abrignoni/iLEAPP.git
We can handle almost all of the requirements with pip:
cd iLEAPP pip install -r requirements.txt
As I am installing on linux I also need the python3-tk package to support the GUI; apt can take care of that for us:
sudo apt install python3-tk
Now that we have iLEAPP installed we can get on with the analysis!
Processing with iLEAPP
The iOS dump used in the CTF was distributed as a TAR archive:
MD5: 09683cf41534735ab1c24dbb898a3a4a SHA1: 1211ed593e5111e45d04077ede3d0cd9728349b0
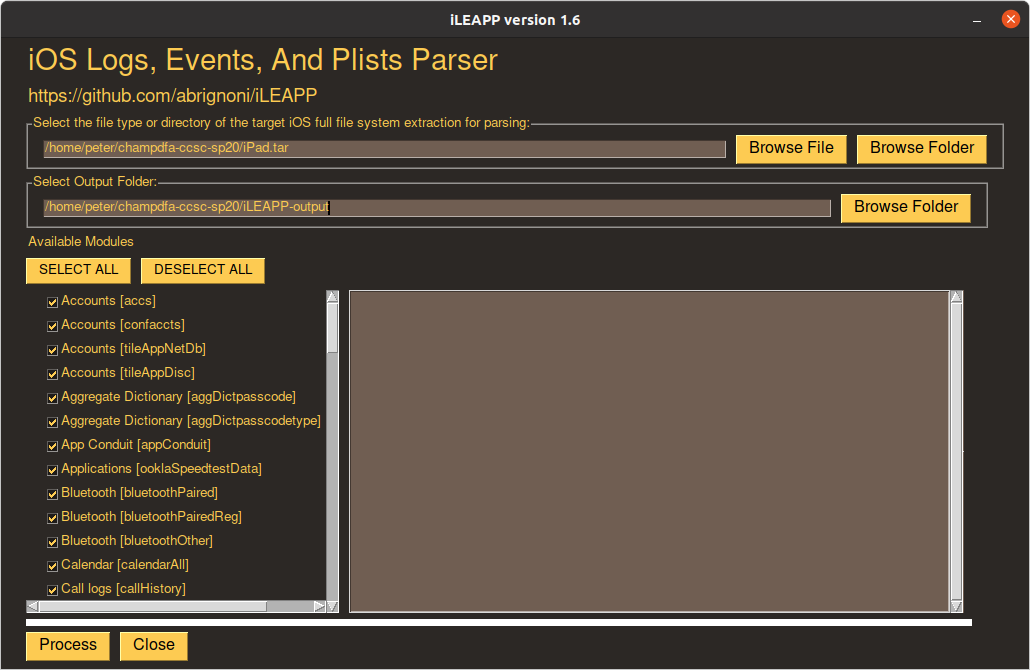
iLEAPP can process the dump directly from the TAR file, or as a directory structure after manual extraction. In this case I chose to process the TAR file directly, using all of the available modules (selected by default):
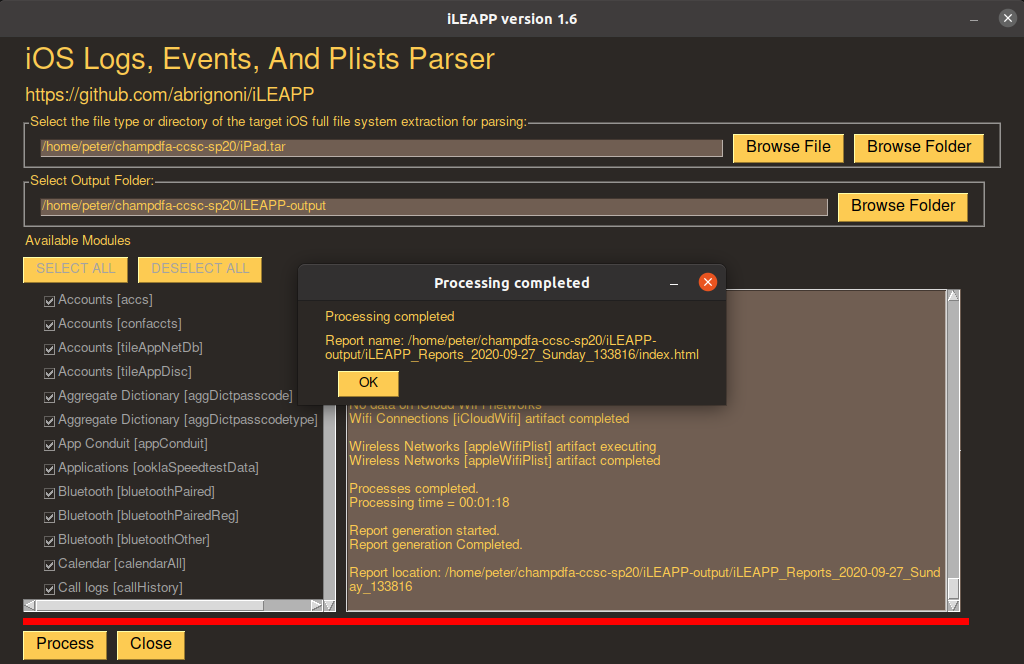
Processing took 1 minute 18 seconds to complete on my rather underpowered virtual machine…
…and produced a nice HTML report of the findings.
As my focus was on playing with iLEAPP rather than fully completing the CTF, I have only answered six of the 19 questions in the iOS analysis section:
01 – I’m just trying to do my iObeSt (50 points)
What ios version is this device on?
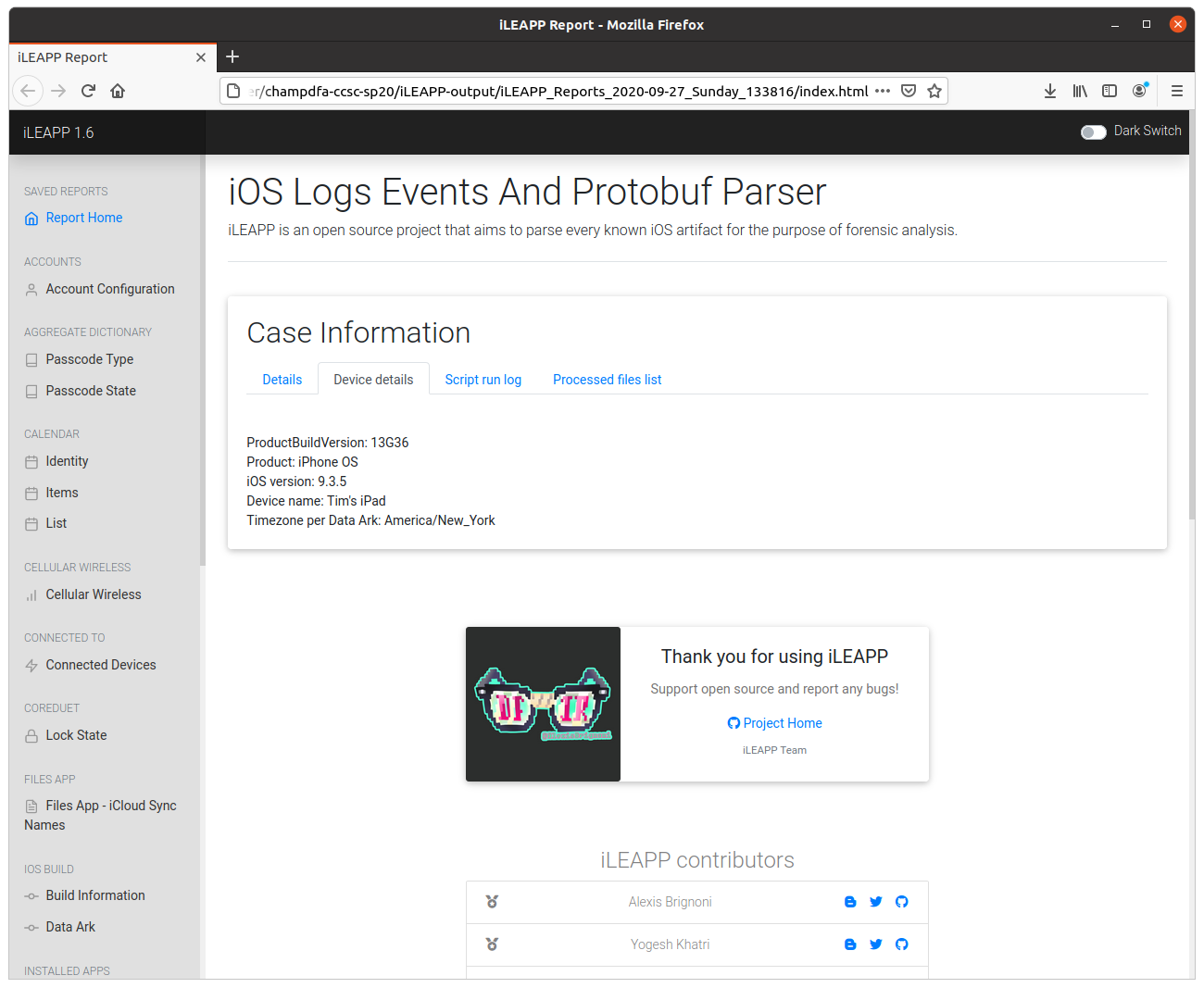
The first question was simple – using the Device Details tab in the Case Information section of the report.
One thing that stood out was that the iOS version was 9.3.5, which is a little outdated in 2020. According to the documentation, the current version of iLEAPP (version 1.6) supports iOS versions 11, 12, and 13. I’m not sure if this made any difference to the analysis that iLEAPP was able to perform.
flag<9.3.5>
03 – The Man, the Myth, the Legend (50 points)
Who is using the iPad? Include their first and last name.
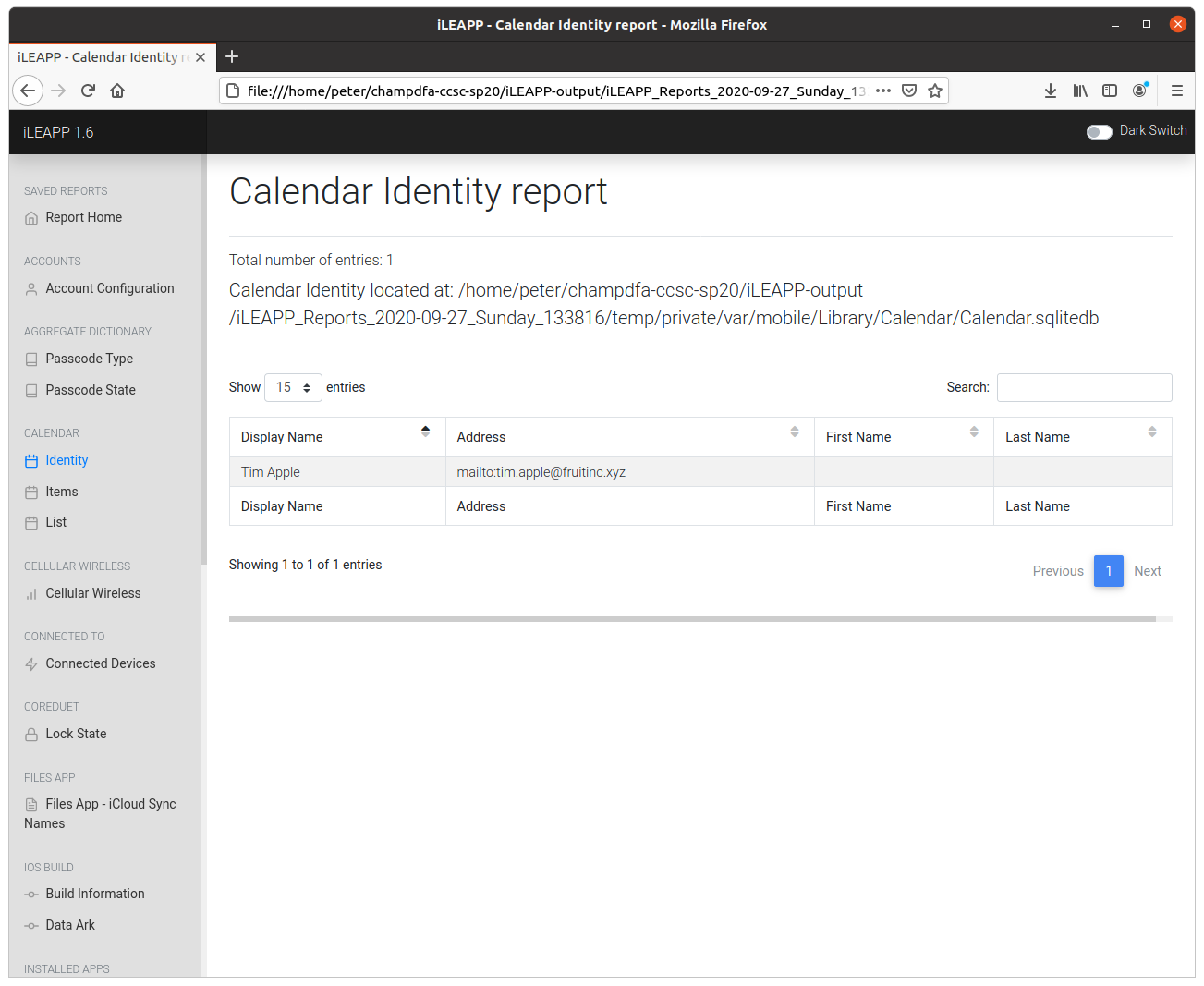
Digging through the iLEAPP report I found the Calendar Identity Report which listed the display name and email address of our old friend Tim Apple.
flag<Tim Apple>
07 – High Fi! (150 points)
What is the name of the WiFi network this device connected to
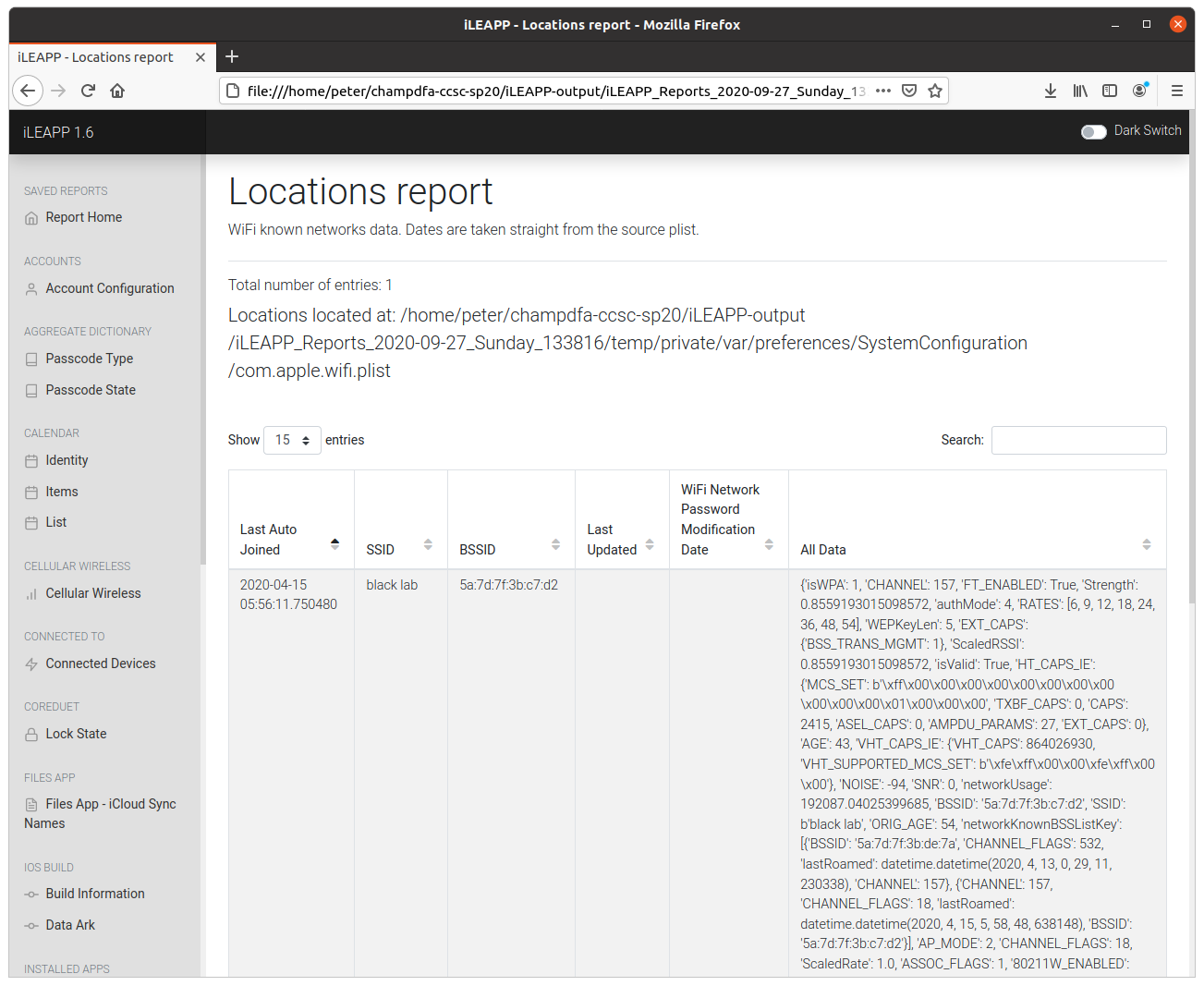
Again, iLEAPP makes this very simple – the report extracts a list of known WiFi networks. In this case there is only one entry, an SSID named black lab.
flag<black lab>
12 – Let me in LET ME INNNNNN (200 points)
What app was used to jailbreak this device?
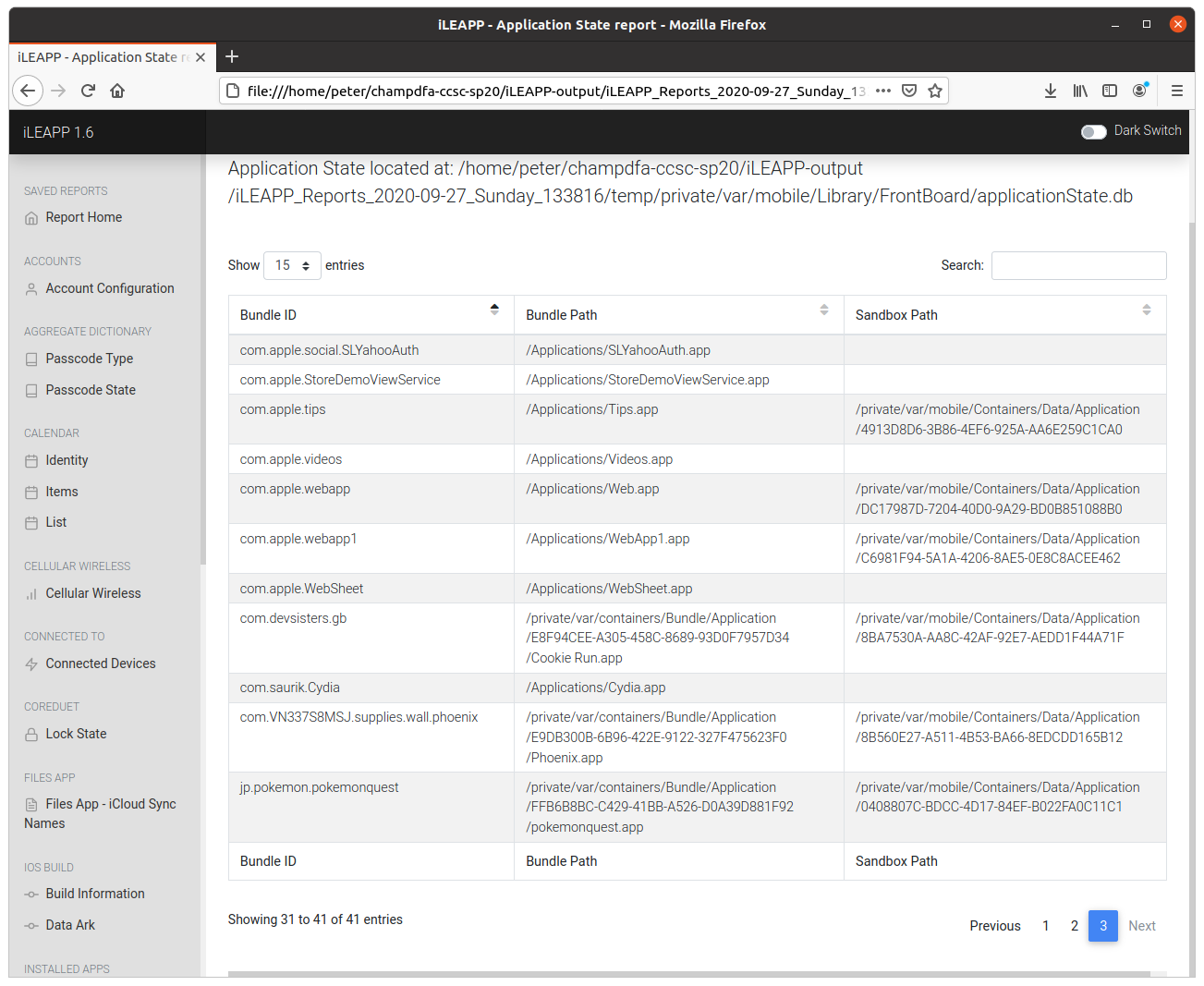
iLEAPP also gives us a nice list of installed applications:
The com.saurik.Cydia package immediately stood out as one of the alternative App Stores commonly installed on jailbroken devices, but after some searching I found that the com.VN337S8MSJ.supplies.wall.phoenix package corresponds to the Phoenix Jailbreak for iOS 9.3.5 and 9.3.6
flag<phoenix>
18 – Interstellar Docking Scene Music (300 points)
Name one of the apps that were on this device’s dock. Provide them in bundle format: com.provider.appname
Going by the high number of CTF points awarded for this question one might expect the answer to be held in some obscure plist, but iLEAPP makes this easy!
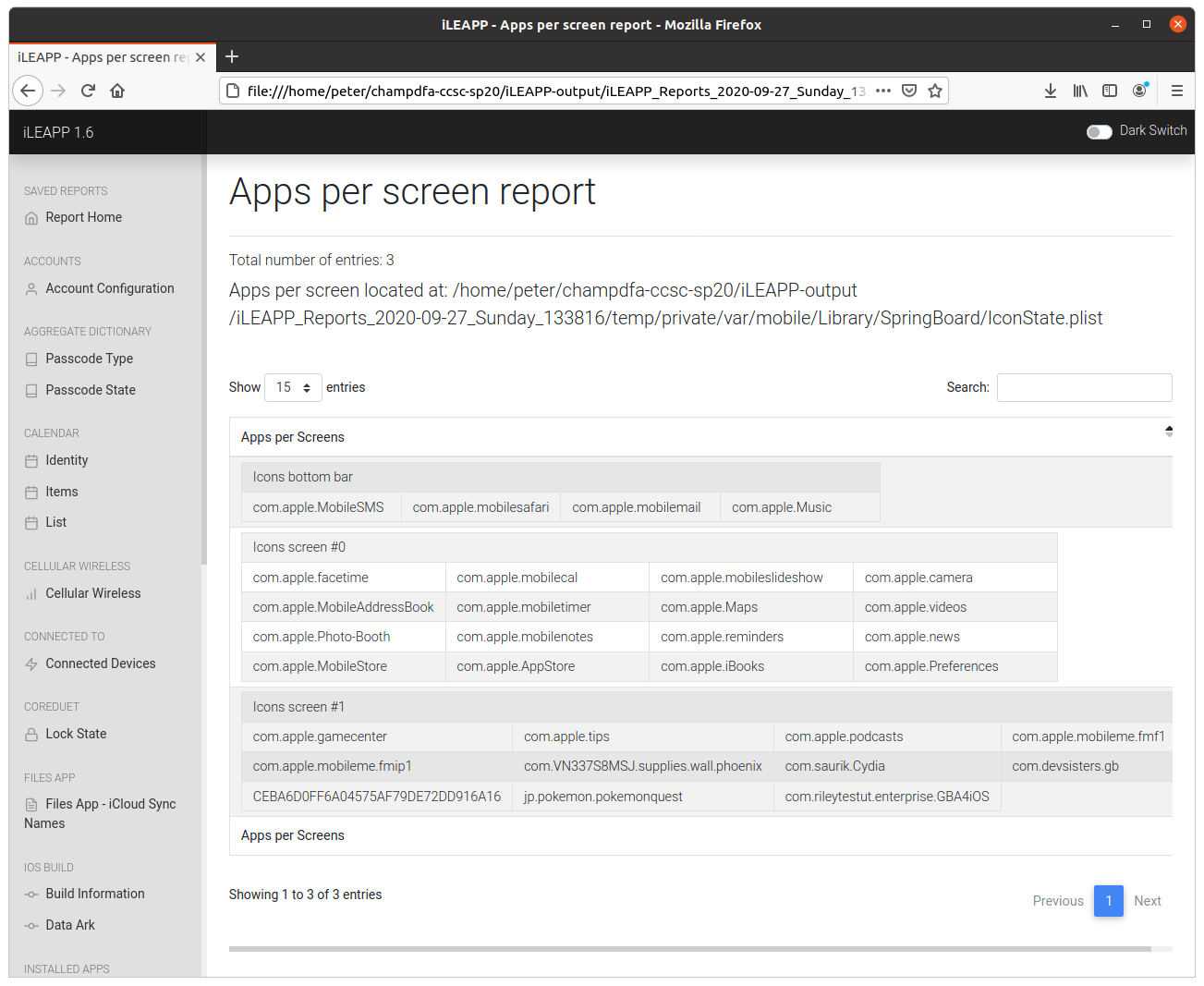
The Apps per Screen report plots the position of each application icon in an easy to follow table, including those in the dock (icons bottom bar). We have four applications to choose from; I submitted the first one, which was accepted as a correct flag.
flag<com.apple.MobileSMS>
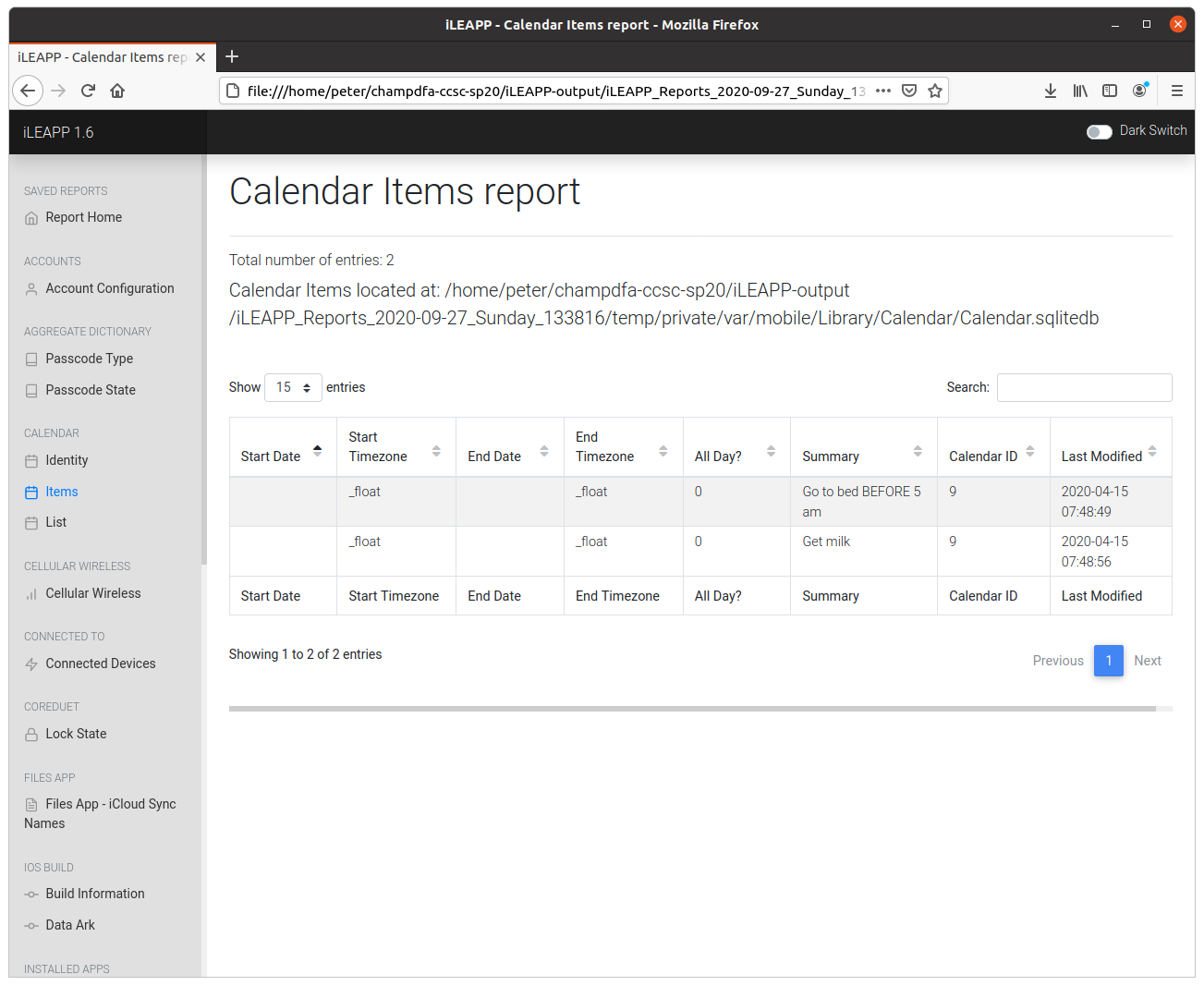
19 – Remind me later (300 points)
A reminder was made to get something, what was it?
Again, another 300-point question easily answered with iLEAPP.
The Calendar Items report lists two reminders; one to “go to bed before 5AM” and another to “get milk“. Easy!
flag<milk>
Summary
Again, this is not a complete write-up of the iOS analysis section of the Champlain College Spring 2020 CTF, and might not even be a complete representation of the current state of iLEAPP! Even so, I think this has shown how powerful a tool iLEAPP is for performing quick analysis of Apple iOS devices, and iLEAPP is regularly updated to support new analysis modules so I fully expect that its capabilities will improve further in future.
While the CTF has now formally closed meaning that no points will be assigned, the challenge site is still available and functioning as of October 2020 if you would like to download the images and have a go yourself. I was able to make quick progress with iLEAPP alone; the most recent version of the SANS Smartphone Forensics poster looks like a great help too for anything that iLEAPP might miss!
1 thoughts on “DFA/CCSC Spring 2020 CTF – Apple iOS Forensics with iLEAPP”