Magnet Forensics have announced a weekly CTF running from October 2020. A new challenge will be released each week on Monday, and the first few are based on an Android filesystem dump. You can find my other Magnet Weekly CTF write-ups here.
MD5: 3bb6abb3bf6d09e3e65d20efc7ec23b1 SHA1: 10cc6d43edae77e7a85b77b46a294fc8a05e731d
Week 1 was pretty straightforward. On to Week 2!
PIP Install (30 points)
What domain was most recently viewed via an app that has picture-in-picture capability?
In the last challenge I didn’t need to do any analysis or parsing of the data, simply read the timestamp of a particular file using FTK Imager. This time I needed to dig a little deeper and used Alexis Brignoni’s ALEAPP to parse the Android filesystem dump.
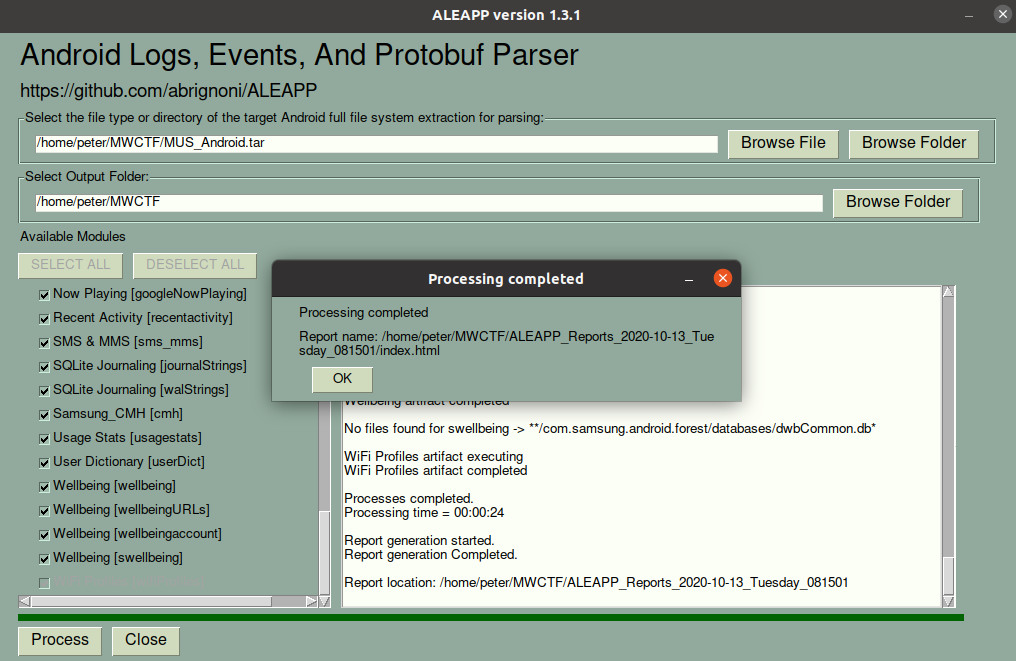
I have previously used iLEAPP to perform analysis of Apple iOS dumps; ALEAPP – the Android Logs Events And Protobuf Parser – works in much the same way, but for Android data. ALEAPP can process the dump directly from the TAR file. I simply started the GUI, set the input and output, and clicked Process.
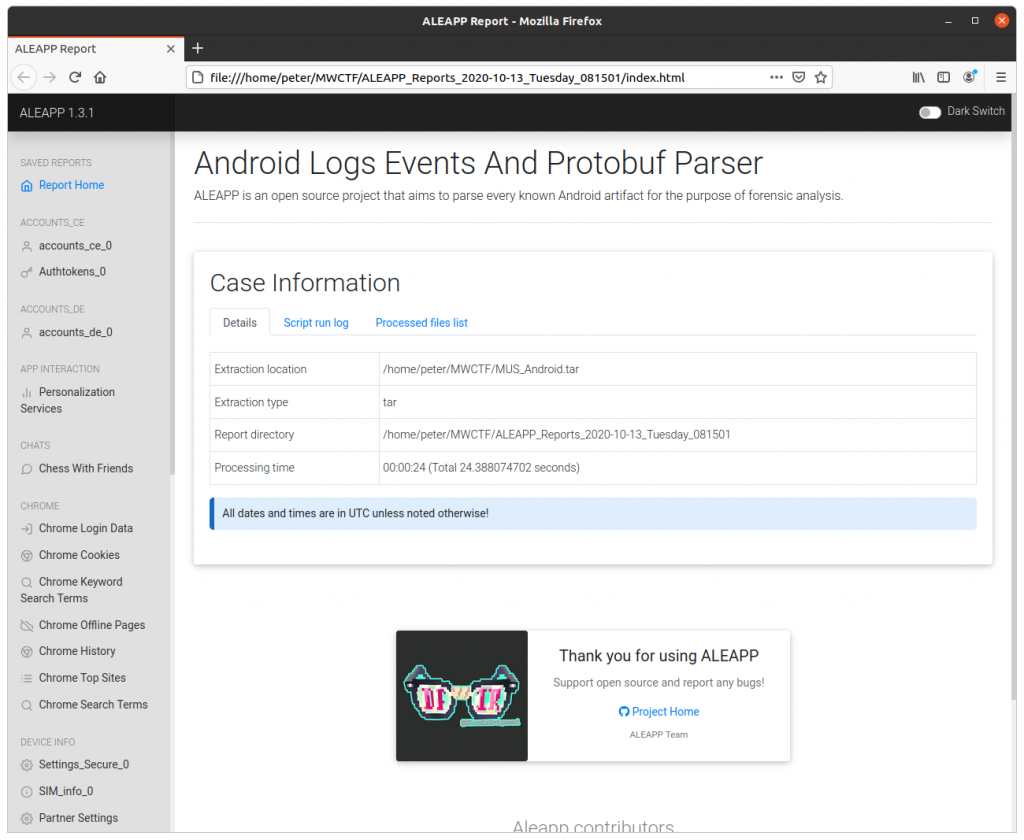
A few seconds later I was presented with a nice HTML report of the analysis.
Given that the question asks about a domain being accessed, I guessed that the Chrome history would be a good place to start. I also found an article containing a list of Android applications which support the picture-in-picture feature – Chrome is listed. Another good sign.
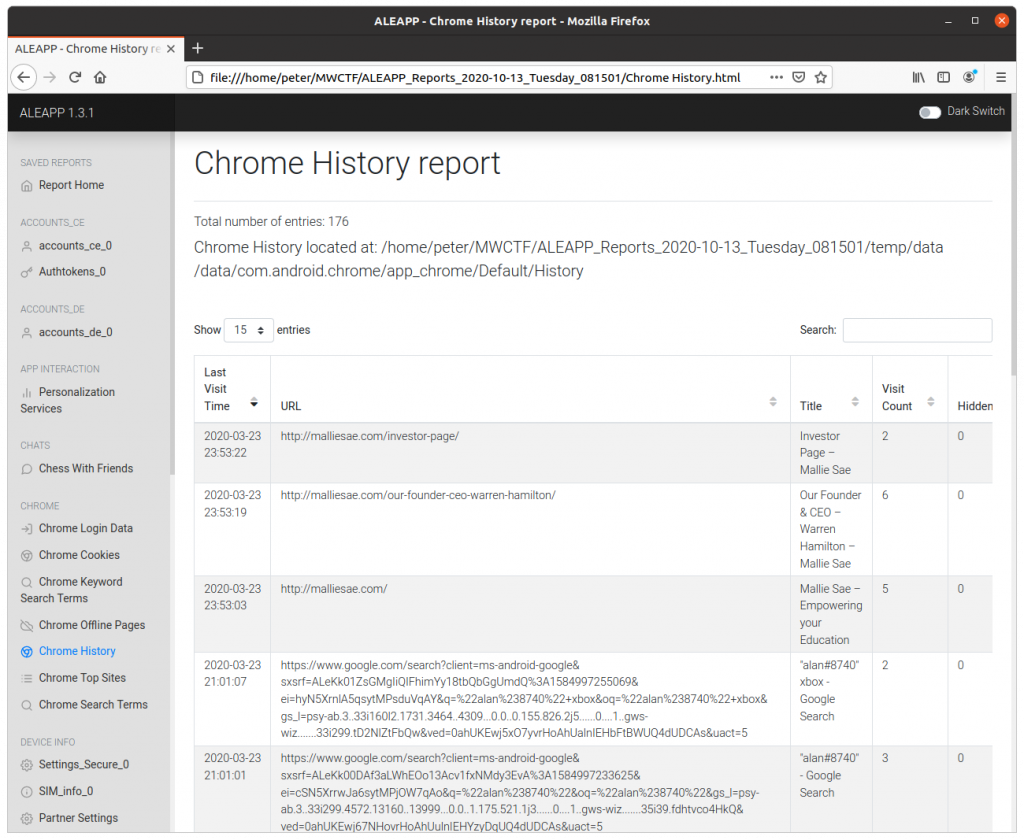
Navigating to the Chrome History report and sorting by the most recent entry, we find the answer to the Week 2 question.
Flag
malliesae.com
1 thoughts on “Magnet Weekly CTF – Week 2 – PIP Install”