Memlabs is a set of six CTF-style memory forensics challenges released in January 2020 by @_abhiramkumar and Team bi0s. This write-up covers Lab 4 – Obsession. You can find the rest of my Memlabs write-ups here.
As usual I started by calculating hashes for the image…
MD5: d2bc2f671bcc9281de5f73993de04df3 SHA1: bf96e3f55a9d645cb50a0ccf3eed6c02ed37c4df
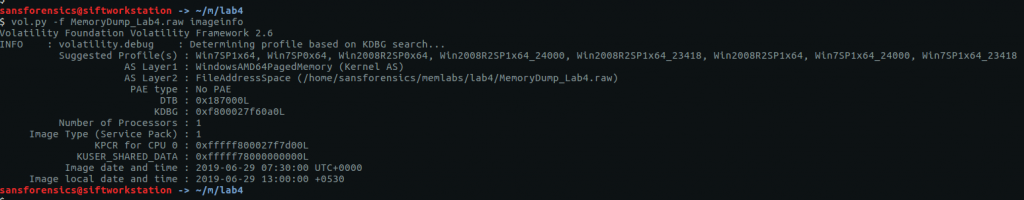
…and running the Volatility imageinfo plugin to determine which profile to use for the rest of the analysis.
vol.py -f MemoryDump_Lab4.raw imageinfo
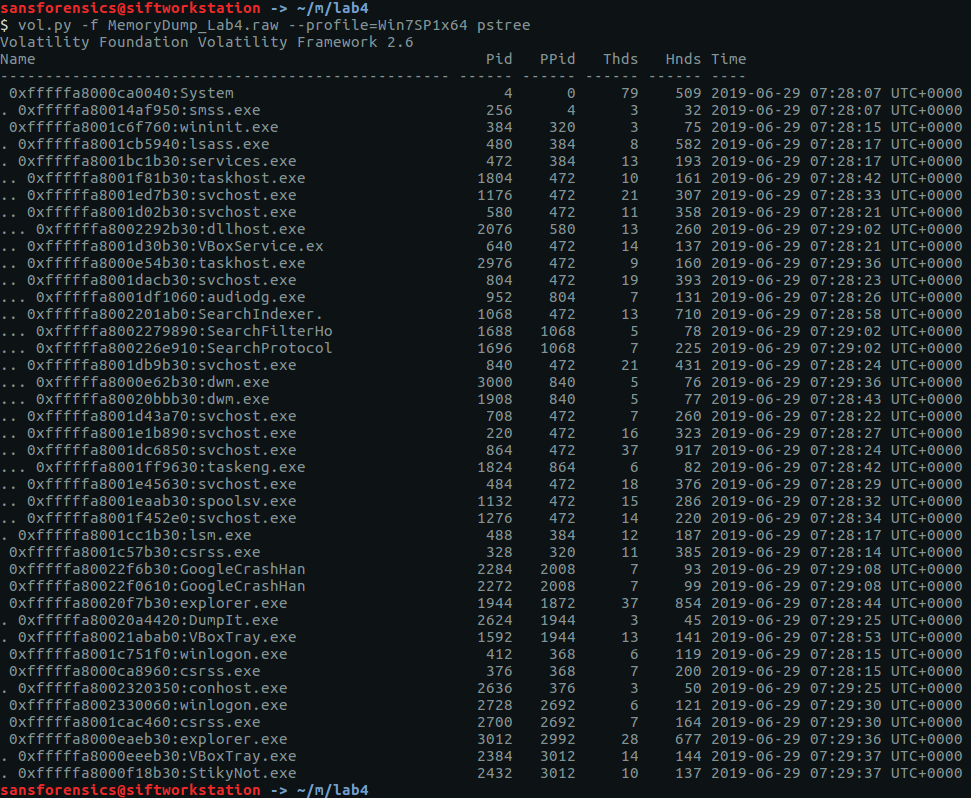
Having chosen Win7SP1x64 from the suggested profiles, I next checked the running processes with the pstree plugin.
vol.py -f MemoryDump_Lab4.raw --profile=Win7SP1x64 pstree
I briefly investigated the StikyNot.exe process but found nothing of interest. Let’s try the filescan plugin instead. I directed the output to a file, and used grep to filter the files in user profile directories, guessing that anything “very important” to the user would be stored there.
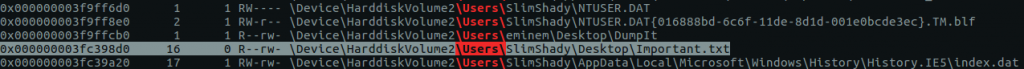
vol.py -f MemoryDump_Lab4.raw --profile=Win7SP1x64 filescan > filescan.txt grep '\\Users\\' filescan.txt
Indeed, examining the filtered list we see a reference to Important.txt in a Desktop directory. My first approach was simply to run the dumpfiles plugin to recover the file from the memory image…
vol.py -f MemoryDump_Lab4.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fc398d0 -D . -n
… but in this case no output was created.
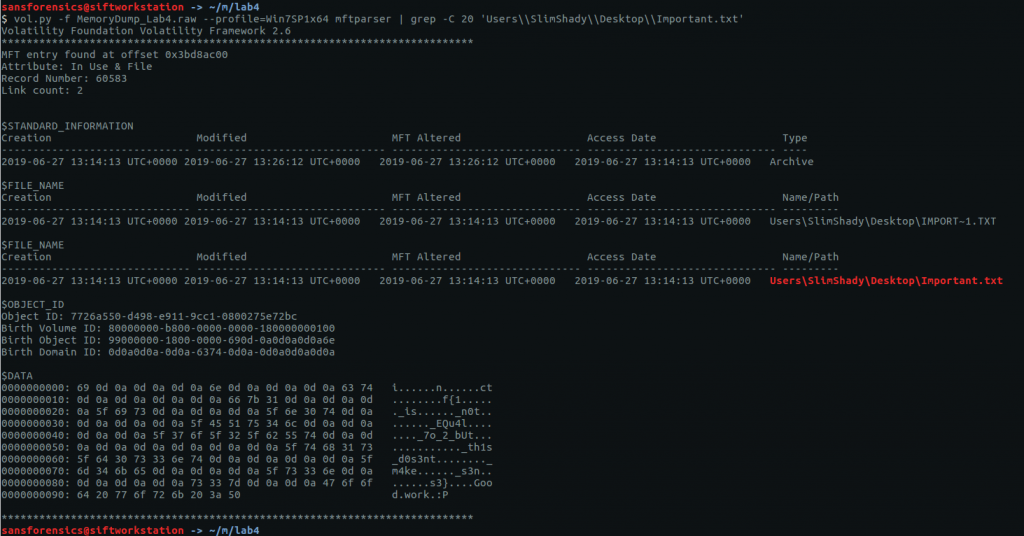
We can’t extract the file directly but there is another place the data might be stored. On an NTFS partition, small files (up to a few hundred bytes) may be stored as resident in the $DATA attribute in the Master File Table (MFT). We can use the mftparser plugin to, well, parse the MFT, and use grep again to filter the relevant entry. The -C 20 argument in my grep command instructs grep to return the 20 lines above and below the matching line.
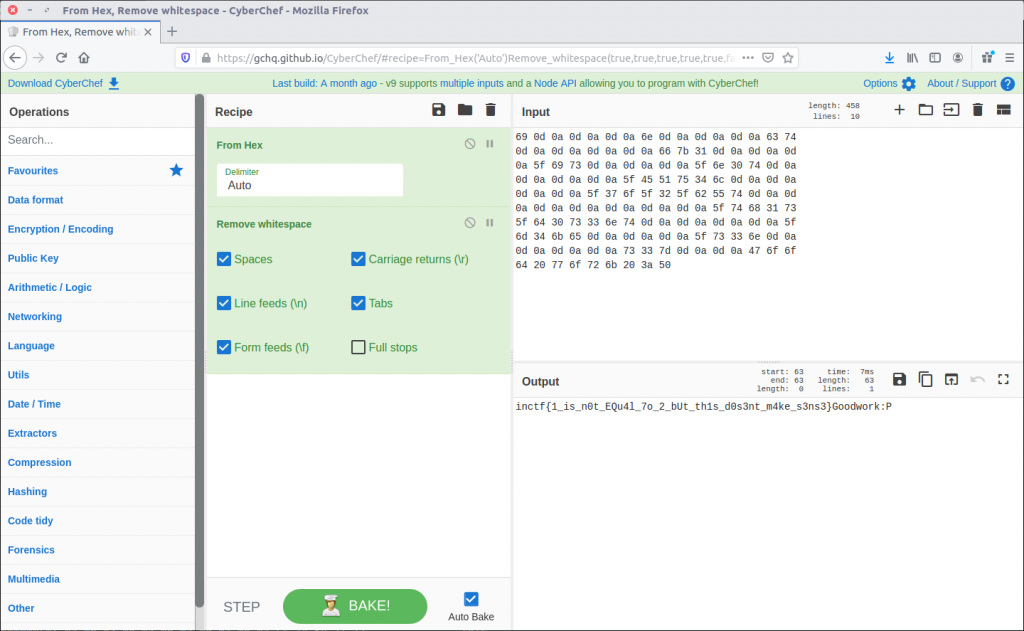
Looking at the $DATA attribute, we can see something that looks like the flag but broken up with whitespace characters; with CyberChef we can easily convert the raw bytes to text then remove these…
… leaving us with our flag to complete the challenge.
inctf{1_is_n0t_EQu4l_7o_2_bUt_th1s_d0s3nt_m4ke_s3ns3}