Magnet Forensics have announced a weekly CTF running from October 2020. A new challenge will be released each week on Monday, and the first few are based on an Android filesystem dump. You can find my other Magnet Weekly CTF write-ups here.
MD5: 3bb6abb3bf6d09e3e65d20efc7ec23b1 SHA1: 10cc6d43edae77e7a85b77b46a294fc8a05e731d
The Week 3 challenge really increased the difficulty, involving a bit of file carving to determine the location a photograph was captured. This week though I mostly relied on luck. And grep.
Animals That Never Forget (25 points)
Chester likes to be organized with his busy schedule. Global Unique Identifiers change often, just like his schedule but sometimes Chester enjoys phishing. What was the original GUID for his phishing expedition?
I really had no idea where to start with this one. Calendar data? ALEAPP says no. I decided to simply extract the evidence TAR file and grep through the dump for phish saving the output for later with tee.
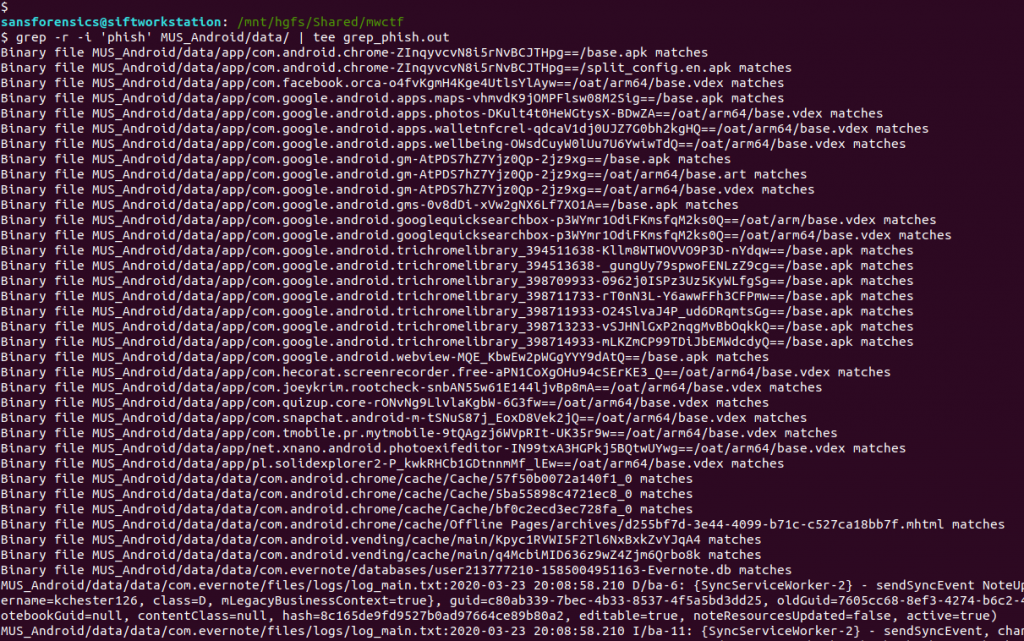
grep -r -i 'phish' MUS_Android/data/ | tee grep_phish.out
Not a bad start. We have a lot of matches in binary files so let’s exclude those from the output and see what’s left.
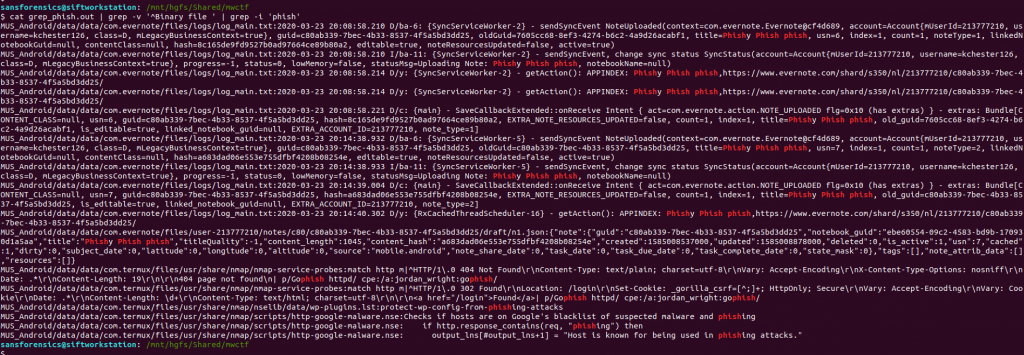
cat grep_phish.out | grep -v '^Binary file ' | grep -i 'phish'
Better! We have a few matches in a log belonging to the Evernote application, and we might even have our answer already!
oldGuid=7605cc68-8ef3-4274-b6c2-4a9d26acabf1
As with Week 3, we only have three attempts to answer this so let’s dig into the log file and see what else we can find.
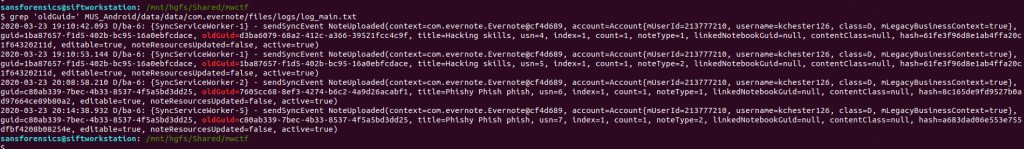
grep 'oldGuid=' MUS_Android/data/data/com.evernote/files/logs/log_main.txt
The oldGuid key appears four times, along with timestamps; the question asks for the original GUID, presumably the earliest one in the file. We can use grep again to show only the lines relating to our phishing note.
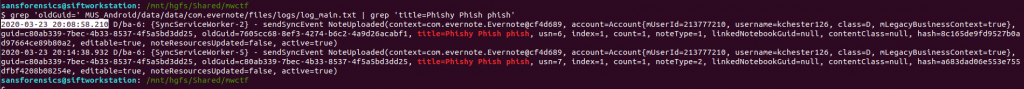
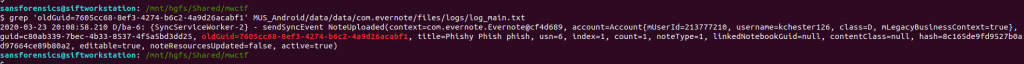
grep 'oldGuid=' MUS_Android/data/data/com.evernote/files/logs/log_main.txt | grep 'title=Phishy Phish phish'
The first hit is the earlier of the two so things are looking good. The screenshot below highlights the oldGuid value.
I think that’s probably enough to verify that we at least have a reasonable answer before burning one of the three attempts. Submit the oldGuid value and we have successfully completed the Week 4 challenge!
Flag
7605cc68-8ef3-4274-b6c2-4a9d26acabf1