In an effort to improve my forensics skills I have been working through publicly available forensics CTFs when I have some free time.
Memlabs is a set of six CTF-style memory forensics challenges released in January 2020 by @_abhiramkumar and Team bi0s. This write-up covers the first memory image which has three flags to uncover.
Unlike most CTFs I have encountered, Memlabs does not actually ask any questions or give hints regarding the flags, only that the flags have the following format:
flag{stage1_is_n0w_d0n3}
No hashes were provided to check against but I calculated the following:
MD5: b9fec1a443907d870cb32b048bda9380 SHA1: 02a58ccf572e6b369934268842551722c4411a60
Let’s go!
Flag 1
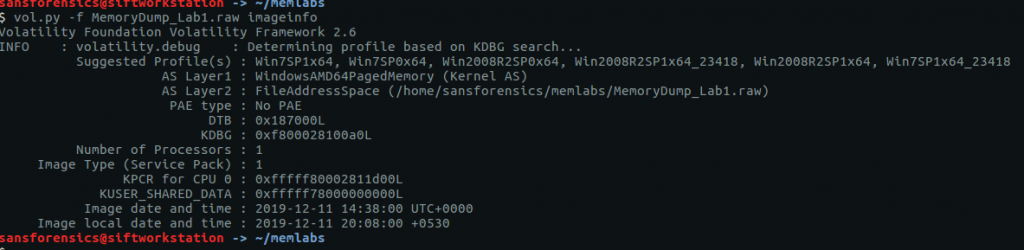
First let’s determine what kind of memory image we are working with. As usual for memory forensics, I’m going to work with Volatility.
vol.py -f MemoryDump_Lab1.raw imageinfo
The first suggestion is Win7SP1x64; this seems like a sensible starting point.
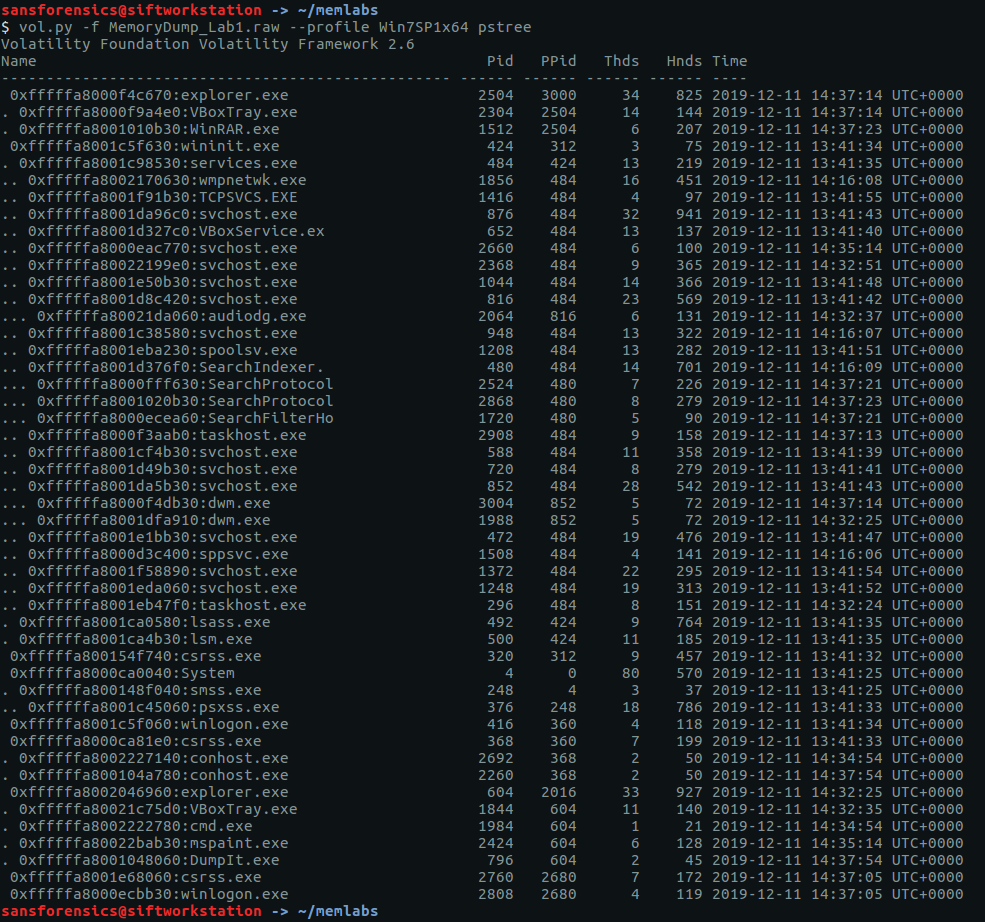
We have no clues as to what we are supposed to be looking for. Let’s check the running processes using the pstree module and see if anything stands out.
vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 pstree
The only processes that stand out are WinRAR.exe (PID: 1512), cmd.exe (PID: 1984), and mspaint.exe (PID: 2424). DumpIt.exe is likely the tool used to capture the memory dump so I am ignoring it for now. We can use the cmdline and consoles modules to show the command that launched these processes, and any console output associated with them.
vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 cmdline -p 1512,1984,2424
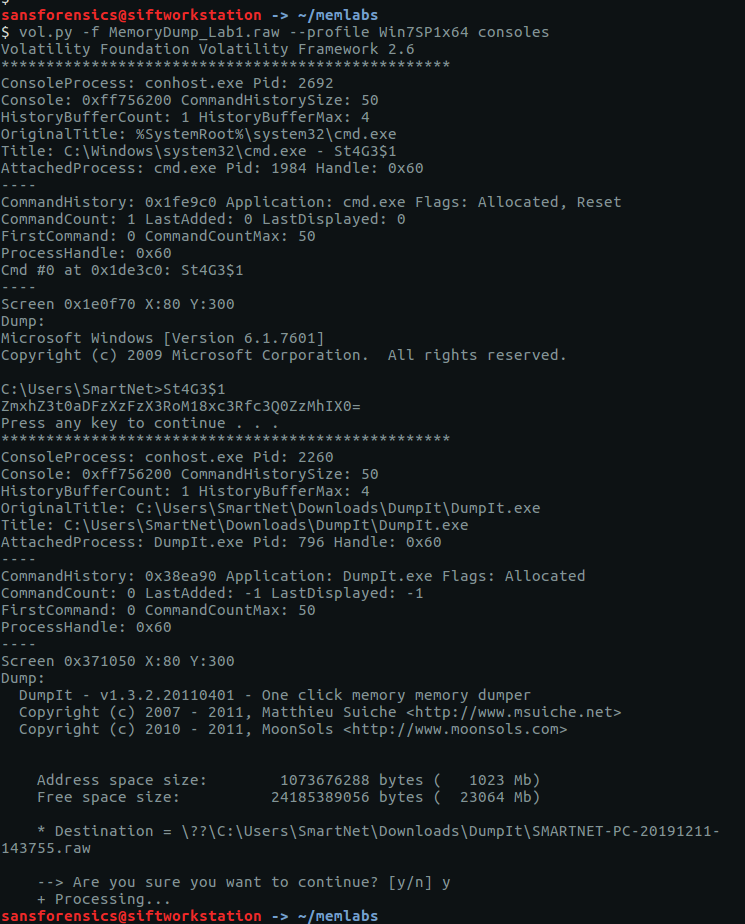
vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 consoles
The output from cmdline tells us that WinRAR.exe was launched with a file called Important.exe which seems, well, important but the consoles plugin shows a command St4Ge$1 being run and the following output:
ZmxhZ3t0aDFzXzFzX3RoM18xc3Rfc3Q0ZzMhIX0=
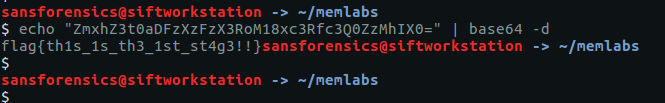
Decoding this from base64 gives us our first flag:
echo "ZmxhZ3t0aDFzXzFzX3RoM18xc3Rfc3Q0ZzMhIX0=" | base64 -d
flag{th1s_1s_th3_1st_st4g3!!}
Flag 2
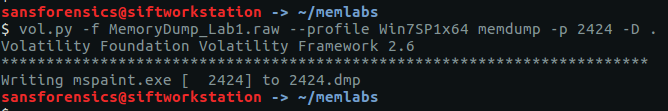
I actually found Flag 3 before Flag 2 as I spotted the reference to Important.rar in the cmdline output, but for ease of reading I’ll keep this order. As I had examined the cmd.exe and WinRAR.exe processes already I guessed that Flag 2 was hidden in the mspaint.exe process, so began by dumping the process memory.
vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 memdump -p 2424 -D .
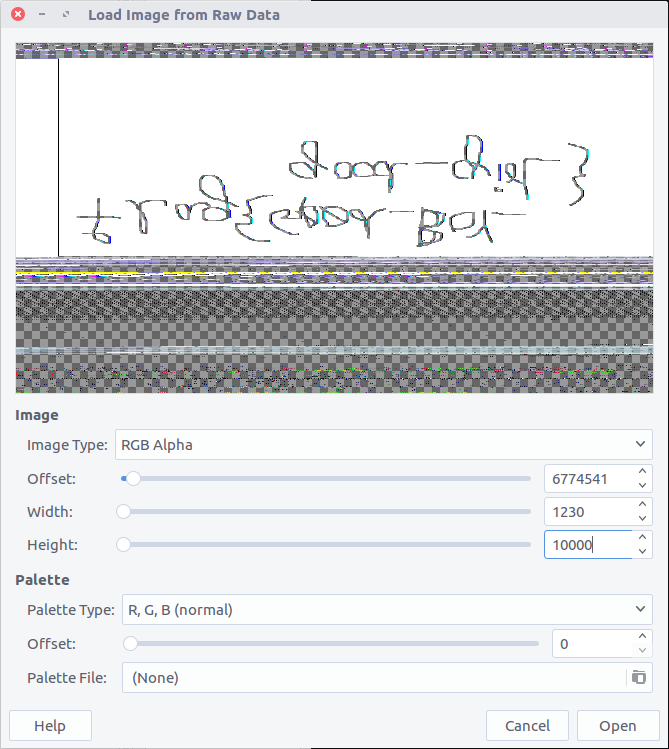
After some Googling I found a blogpost detailing how to extract RAW images from memory dumps. I renamed the dump from 2424.dmp to 2424.data and opened it up with the GIMP image editing suite, setting the Image Type to RGB Alpha, and fiddling with the Offset, Width, and Height values through trial and error until I got something that looked intelligible.
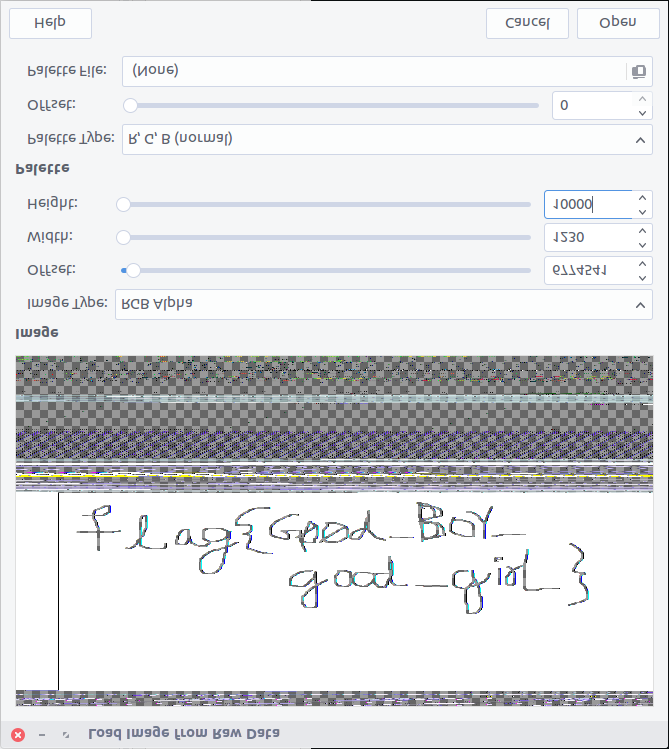
That’s definitely text but not very easy to read. I’m better with Volatility than with GIMP so I took a screenshot of the image preview and flipped it vertically, revealing the flag.
flag{G00d_BoY_good_girL}
Flag 3
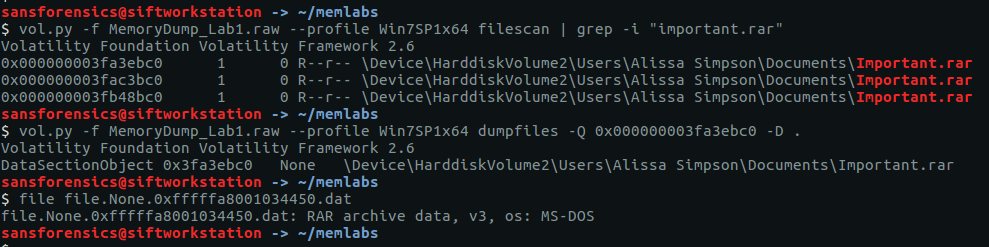
The output from the cmdline module showed that WinRAR.exe had been launched with a file called Important.rar. Lets extract that from the memory image and take a look.
vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 filescan | grep -i "important.rar" vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 dumpfiles -Q 0x000000003fa3ebc0 -D . file file.None.0xfffffa8001034450.dat
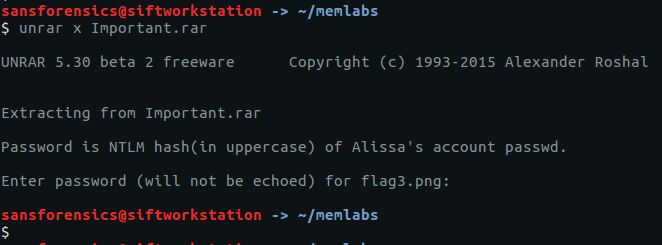
I renamed the file to Important.rar and tried extracting the contents.
unrar x Important.rar
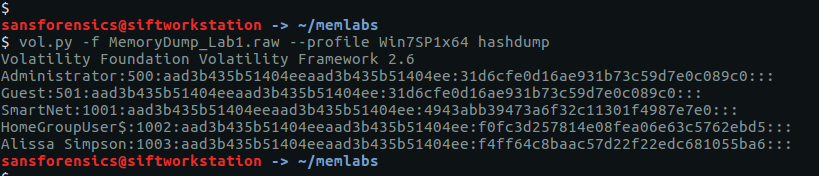
Unfortunately we need a password. Fortunately the password hint tells us where to find it. We can use the hashdump module to dump the NTLM hashes.
vol.py -f MemoryDump_Lab1.raw --profile Win7SP1x64 hashdump
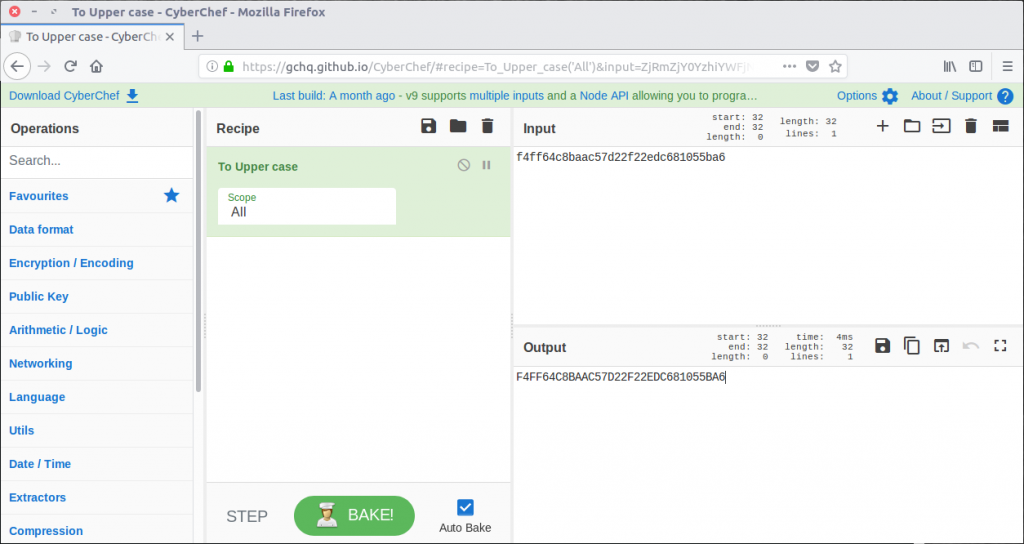
We only need the second part of the hash, but we do need to convert it to upper-case first. Rather than doing it manually I used CyberChef to do it for me.
Now we have the password we can extract the archive and view its contents – a PNG image containing our flag.
flag{w3ll_3rd_stage_was_easy}
Despite completing the first challenge I found the lack of direction or motivation incredibly frustrating. The whole point of forensic investigation is to follow a trail, building on what has been found already to come to a specified conclusion. Real investigations have a purpose. Why was this memory dump captured in the first place? Why are you asking me to take the time to do some analysis? I did learn a new technique in finding Flag 2, but for now I am skipping the rest of Memlabs to work on something more representative of real-world DFIR.

1 thoughts on “Memlabs Memory Forensics Challenges – Lab 1 Write-up”