Memlabs is a set of six CTF-style memory forensics challenges released in January 2020 by @_abhiramkumar and Team bi0s. I completed and published my write-up of Lab 1 in February 2020, but skipped the rest of the challenges due to the general wild-goose-chase approach of simply running Volatility plugins and searching the output for interesting strings.
That was until I saw Jessica Hyde mention the Memlabs challenges on Twitter during the SANS DFIR Summit, and noticed that they had been updated to include some context about why the analysis was needed. With my main complaint from Lab 1 taken care of I jumped back in, starting with Lab 2 – A New World.
As usual, I started by confirming the MD5 and SHA1 hashes of the memory image…
MD5: ddb337936a75153822baed718851716b SHA1: 3ee71b2507e6b5b15bb2e5f97bf809ef7c85d810
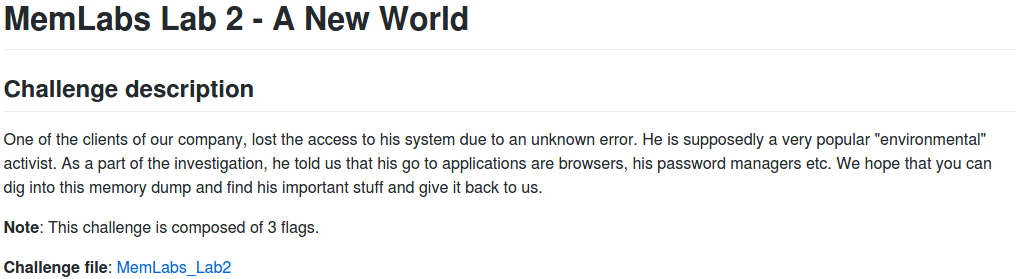
And by determining the correct profile for Volatility using the imageinfo plugin:
vol.py -f MemoryDump_Lab2.raw imageinfo
The output gives us a number of suggestions; Win7SP1x64 will do for now.
The challenge contains three flags, but the order is not important. I am presenting this write-up in the order that I found the flags – Stage 3, Stage 2, then Stage 1.
Stage 3
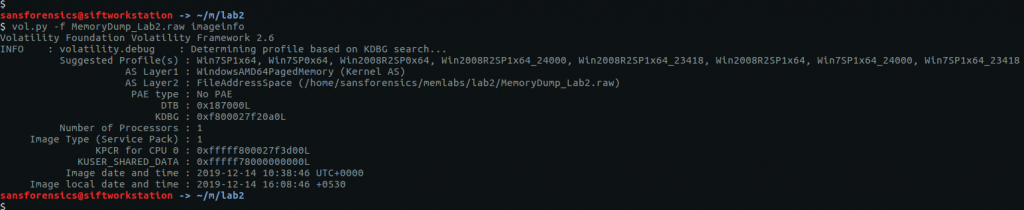
The challenge description mentions that web browsers and password managers. Checking the running processes with the pstree plugin shows that Chrome and the KeePass password manager were running when the dump was made. Let’s start with Chrome.
vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 pstree
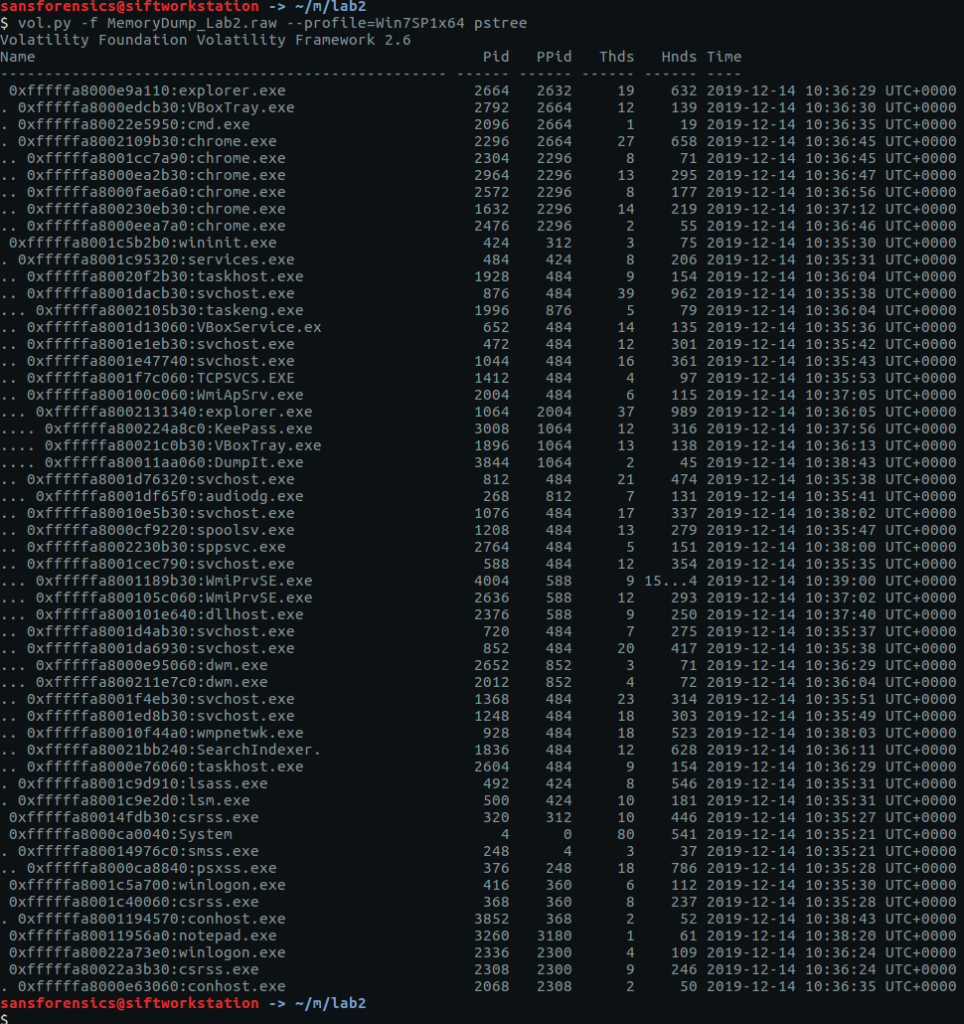
The filescan plugin will produce a list of all of the file objects within the memory dump; it can take some time to run so I redirected the output to a file to speed up grep searches later on.
vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 filescan > filescan.txt head filescan.txt
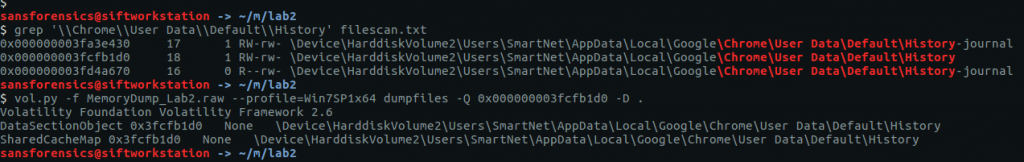
Using grep to search for the location of the Chrome History file we can find and extract the database for analysis using the dumpfiles plugin.
grep '\\Chrome\\User Data\\Default\\History' filescan.txt vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fcfb1d0 -D .
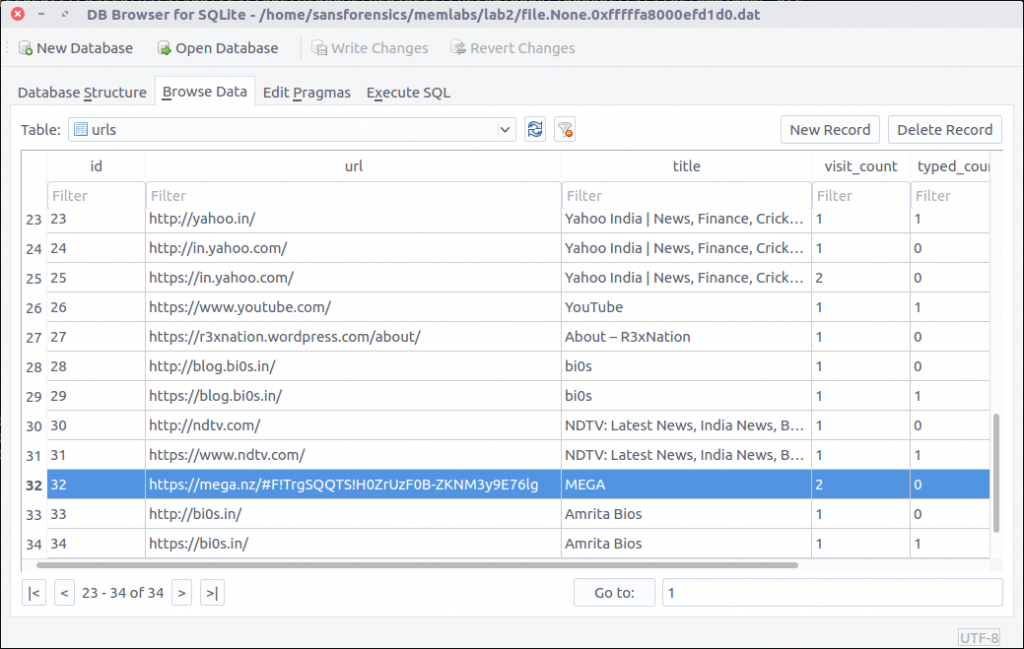
The History file is a SQLite database which we can explore with the sqlite3 command-line tool, or with a GUI application such as DB Browser for SQLite.
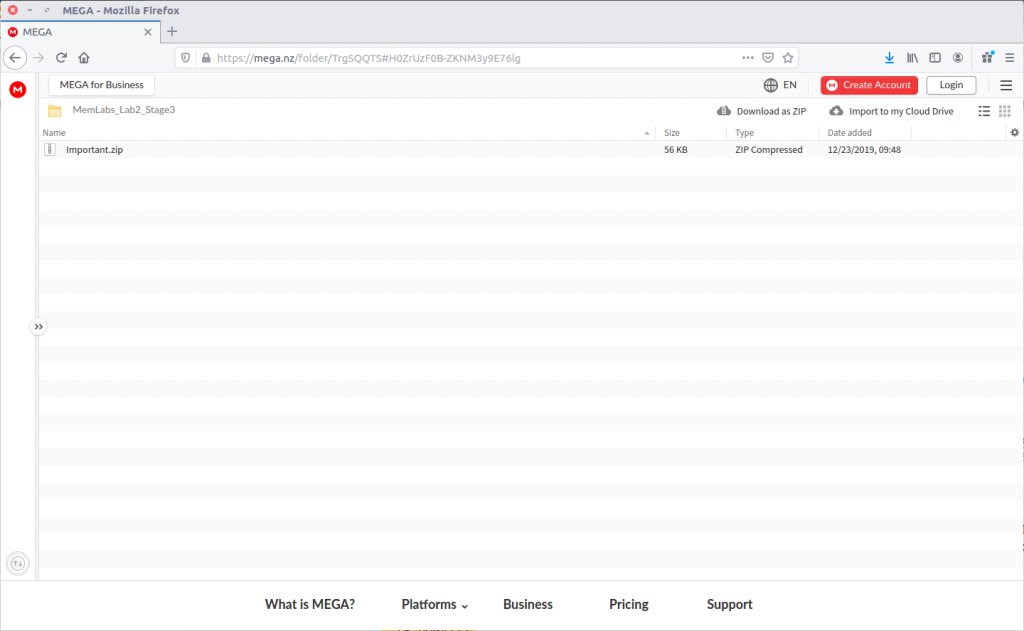
Browsing the database we see that the MEGA file-sharing website was visited; let’s check that out.
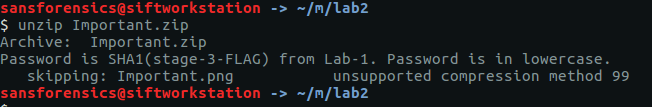
The directory title – MemLab_Lab2_Stage3 – is promising but the ZIP file is password protected.
Fortunately we already know the flags from Lab 1, and CyberChef can easily calculate the SHA1 hash:
6045dd90029719a039fd2d2ebcca718439dd100a
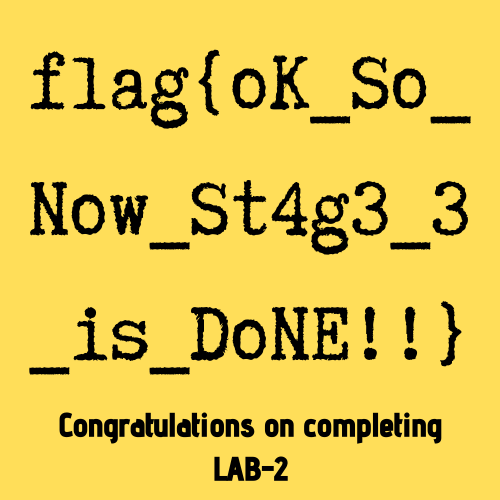
The password is accepted and Important.png is extracted, giving us our first flag (actually for Stage 3, but nevermind).
flag{oK_So_Now_St4g3_3_is_DoNE!!}
Stage 2
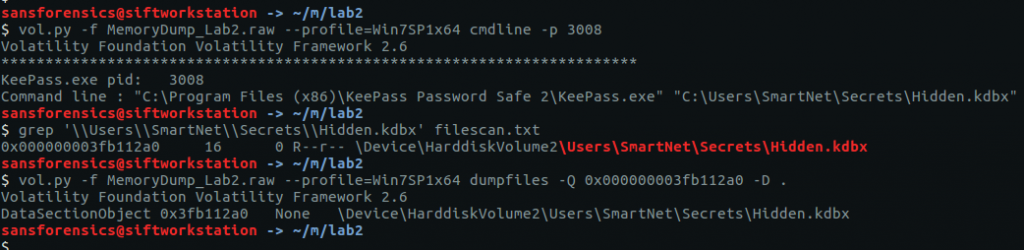
We have investigated the browser history, now let’s take a look at KeePass. We know the KeePass Process ID (3008) from the pstree output earlier. By checking the command-line associated with the KeePass process using the cmdline plugin we can find the location of the KeePass database file, then extract it from the memory dump in the same way as the Chrome History file.
vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 cmdline -p 3008 grep '\\Users\\SmartNet\\Secrets\\Hidden.kdbx' filescan.txt vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fb112a0 -D .
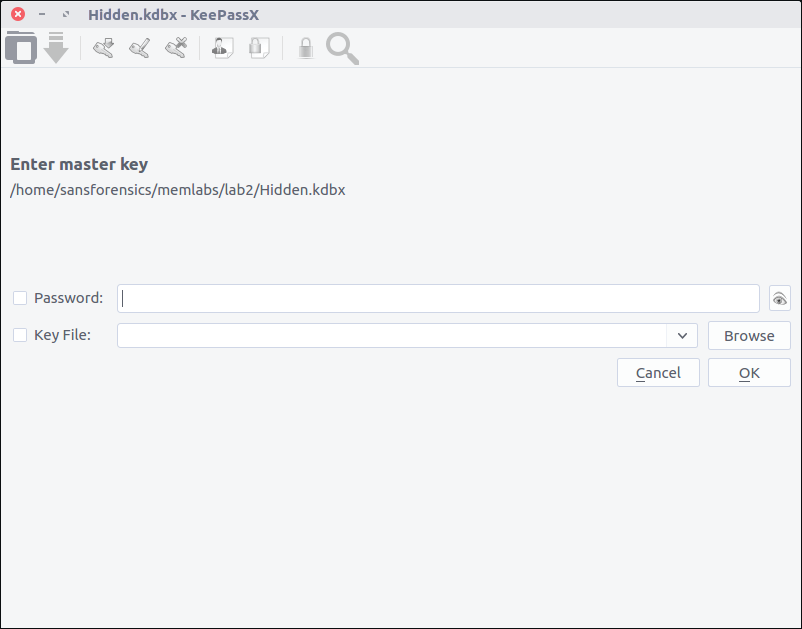
After installing KeePassX on my SIFT VM, I can open the file but require a password before I can actually view any of the contents.
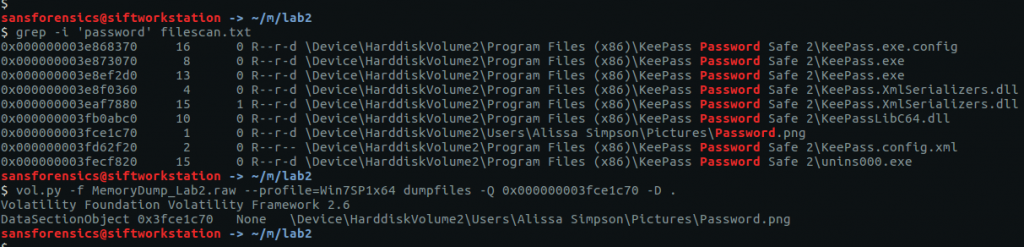
I got lucky with grep searches over the saved filescan output from earlier and was able to extract a file named Password.png
grep -i 'password' filescan.txt vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fce1c70 -D .
Opening the extracted PNG file, we see the following:
The lower right-hand corner of the image contains the following text:
Psst!! password is P4SSw0rd_123
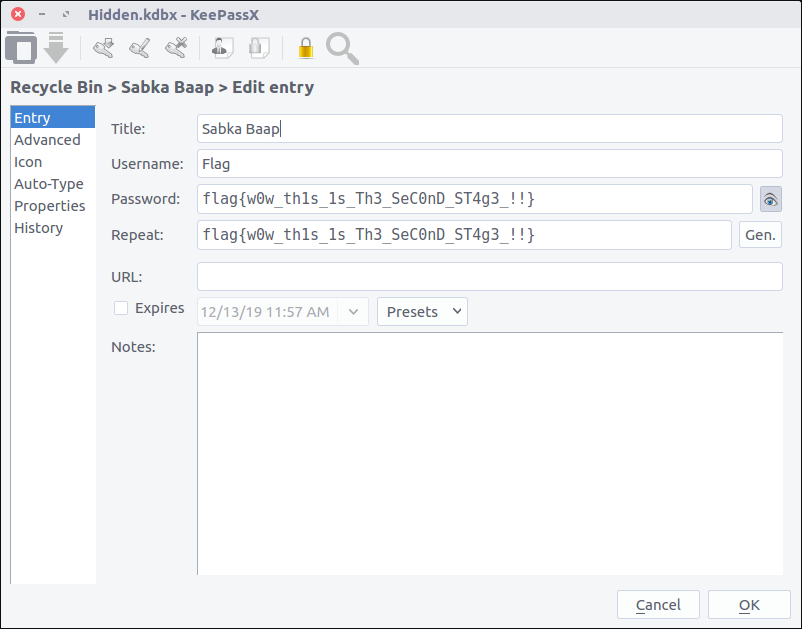
After entering the newly acquired password into KeePassX, we can browse the stored credentials and find the flag for Stage 2.
flag{w0w_th1s_1s_Th3_SeC0nD_ST4g3_!!}
Stage 1
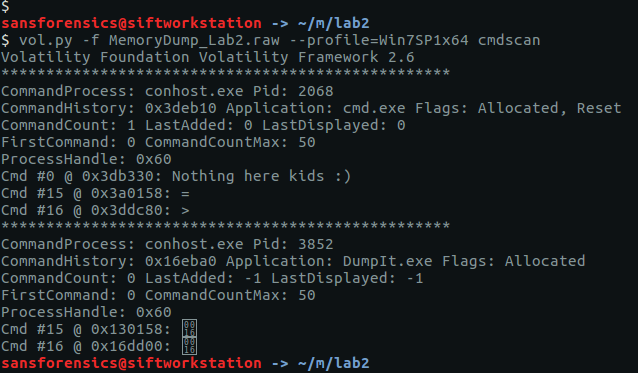
While working on Stage 2 I ran the cmdscan plugin along with cmdline. The cmdscan plugin didn’t return anything related to KeePass, but it did show some unusual output from a cmd.exe shell.
vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 cmdscan
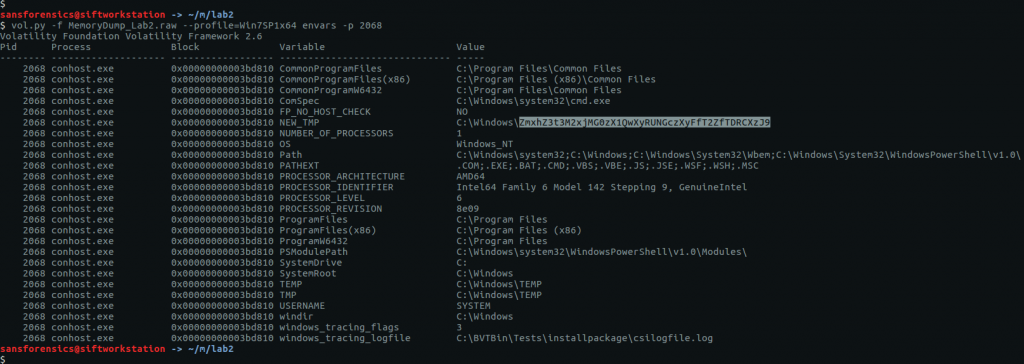
The challenge description emphasises that the owner of the system is an environmental activist; pulling out the environment variables for this process (2068) with the envvars plugin gives us the following:
vol.py -f MemoryDump_Lab2.raw --profile=Win7SP1x64 envars -p 2068
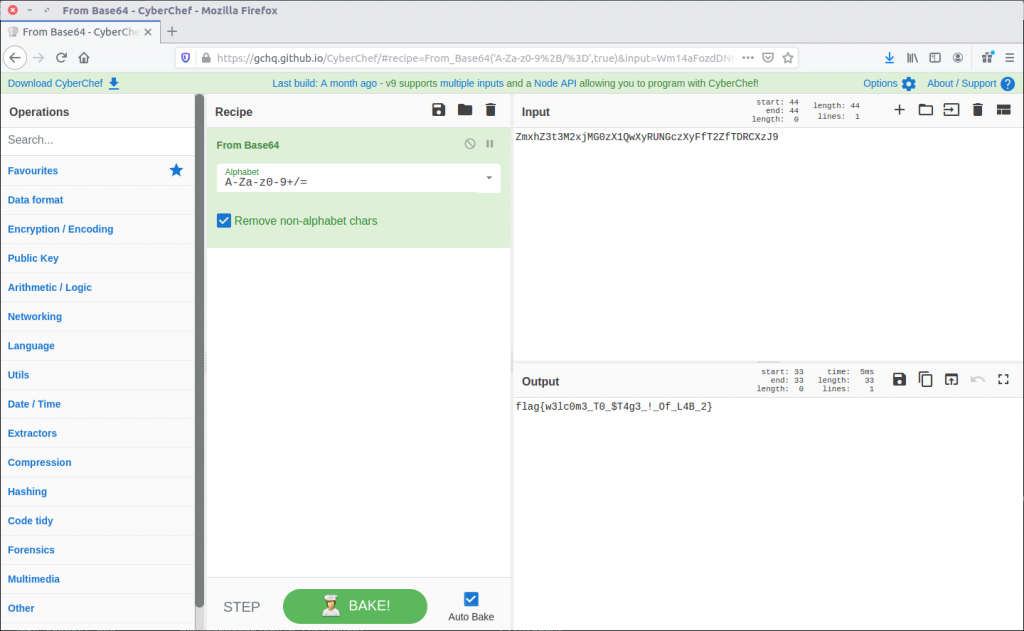
The environment variable NEW_TMP contains what appears to be a base64 string:
ZmxhZ3t3M2xjMG0zX1QwXyRUNGczXyFfT2ZfTDRCXzJ9
Going back to CyberChef, we can decode this with ease and return our final flag for Lab 2.
flag{w3lc0m3_T0_$T4g3_!_Of_L4B_2}
1 thoughts on “Memlabs Memory Forensics Challenges – Lab 2 Write-up”