In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. This series of write-ups covers the network forensics section. As the questions were split over multiple PCAP files (shell, smb, dhcp, network, dns, and https), I have decided to split my write-ups by PCAP for ease of reading.
This write-up covers the questions relating to the dhcp PCAP file.
MD5: 166d1b3b82e23bbca694391b97d728e0 SHA1: 837ede0bb272c4a10163934e68320549a5c40498
01 – I will assit (50 points)
What IP address is requested by the client?
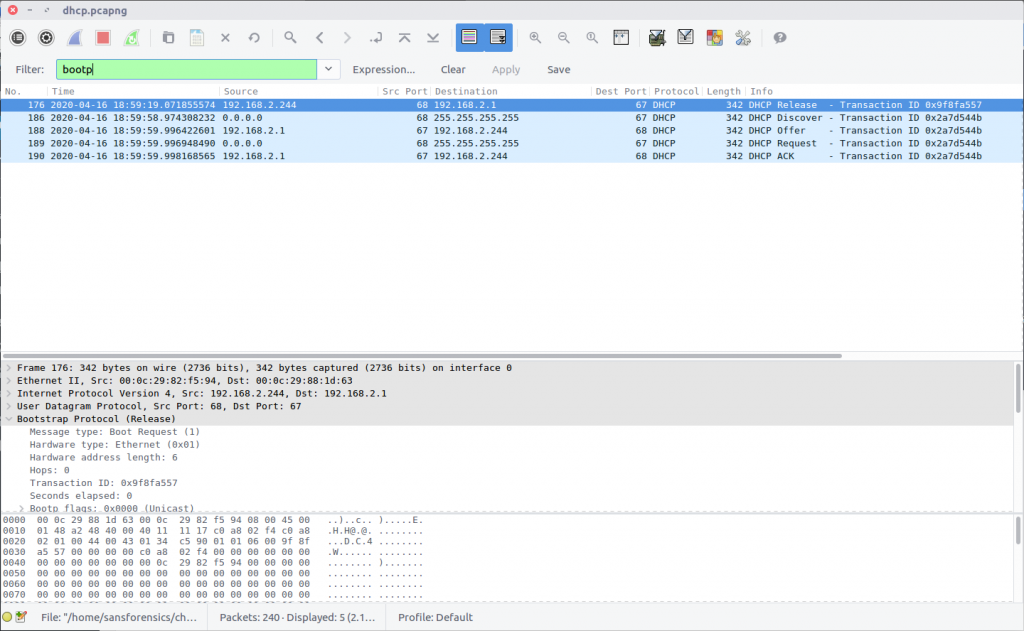
Wireshark does not have a built-in Display Filter specifically for DHCP traffic, but it does have one for the underlying protocol BOOTP.
bootp
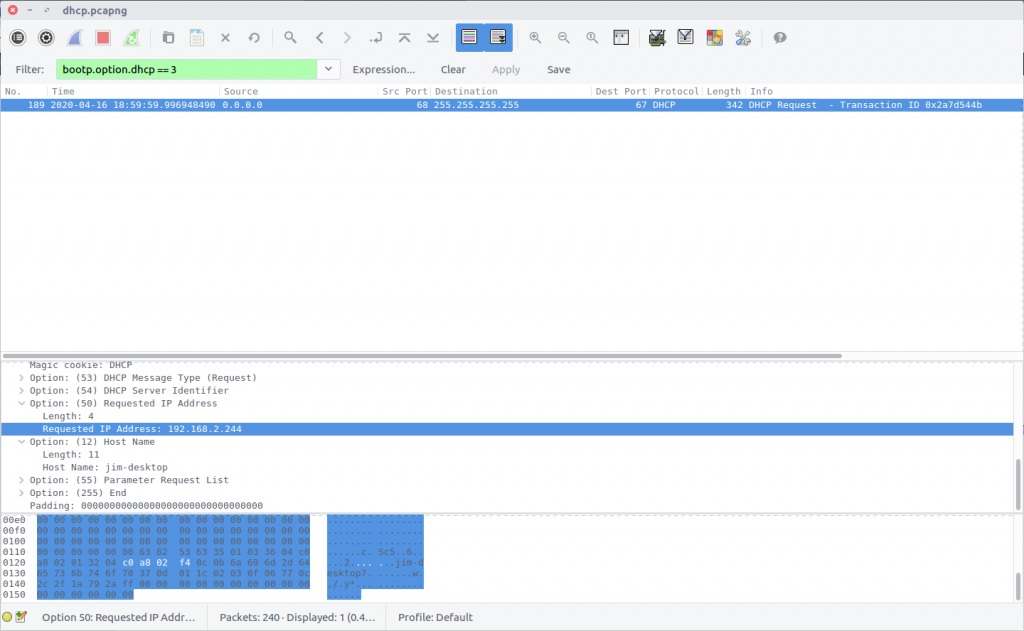
As there are only five DHCP packets in the capture we could simply read through them all to answer the questions, but let’s try to be a bit more specific with Wireshark. Reading the Wireshark wiki DHCP page and the BOOTP Display Filter Reference we find that we can filter on the BOOTP option type to filter only DHCP Requests.
bootp.option.dhcp == 3
This Display Filter returns a single packet containing the DHCP request, including the Requested IP Address field.
flag<192.168.2.244>
02 – Shark01 (50 points)
What is the transaction ID for the DHCP release?
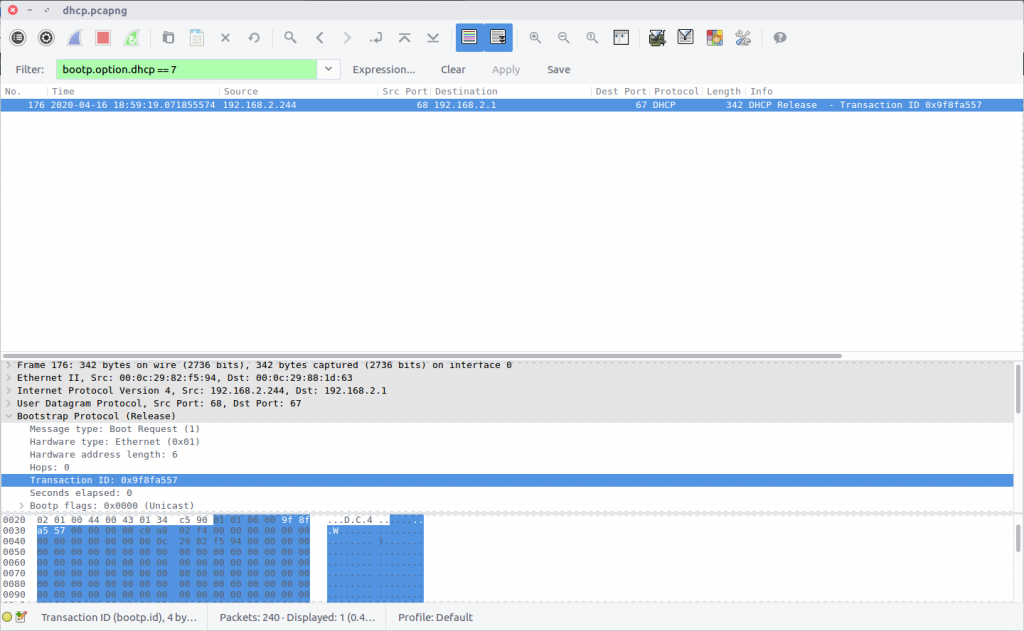
Using the Wireshark wiki and documentation from Question 1, we can filter the DHCP Release with the following Display Filter:
bootp.option.dhcp == 7
Examining the packet details we find the Transaction ID field.
flag<0x9f8fa557>
03 – Who speaks (50 points)
What is the MAC address of the client?
Format: flag<XX:XX:XX:XX:XX:XX>
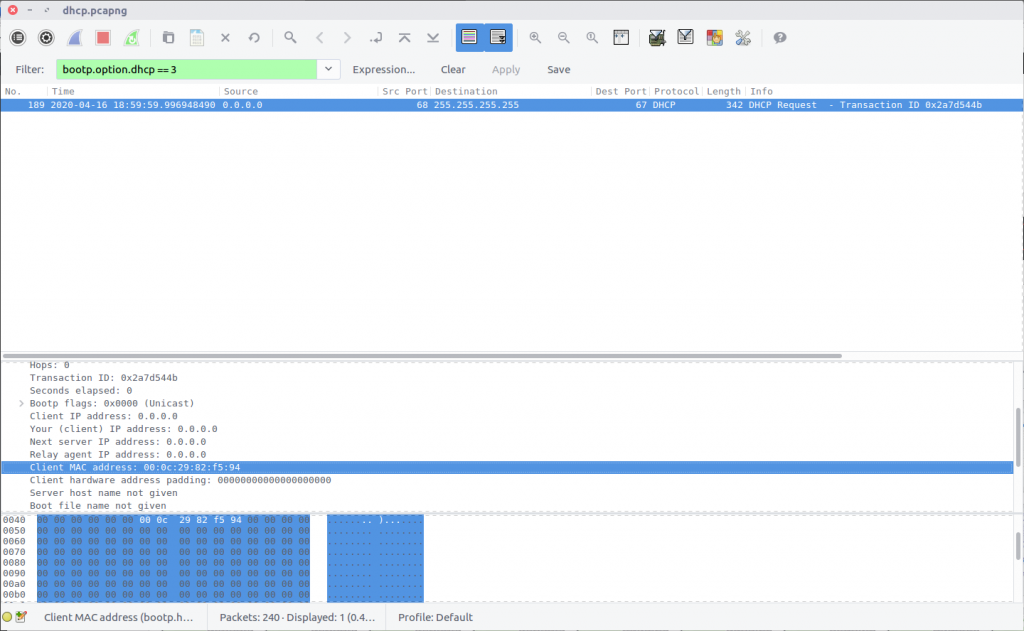
Moving back to the DHCP Request from Question 1, we can simply examine the packet details and read the Client MAC Address field.
bootp.option.dhcp == 3
flag<00:0C:29:82:F5:94>
4 thoughts on “DFA/CCSC Spring 2020 CTF – Wireshark – dhcp.pcapng Write-up”