In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. This series of write-ups covers the network forensics section. As the questions were split over multiple PCAP files (shell, smb, dhcp, network, dns, and https), I have decided to split my write-ups by PCAP for ease of reading.
This write-up covers the questions relating to the network PCAP file.
MD5: d6d5d77b88d73ae4299094a6888226a2 SHA1: fc5ba6363a3ed27e17d9c117a92f1a1395b90f98
01 – Please give (50 points)
What is the IP address that is requested by the DHCP client?
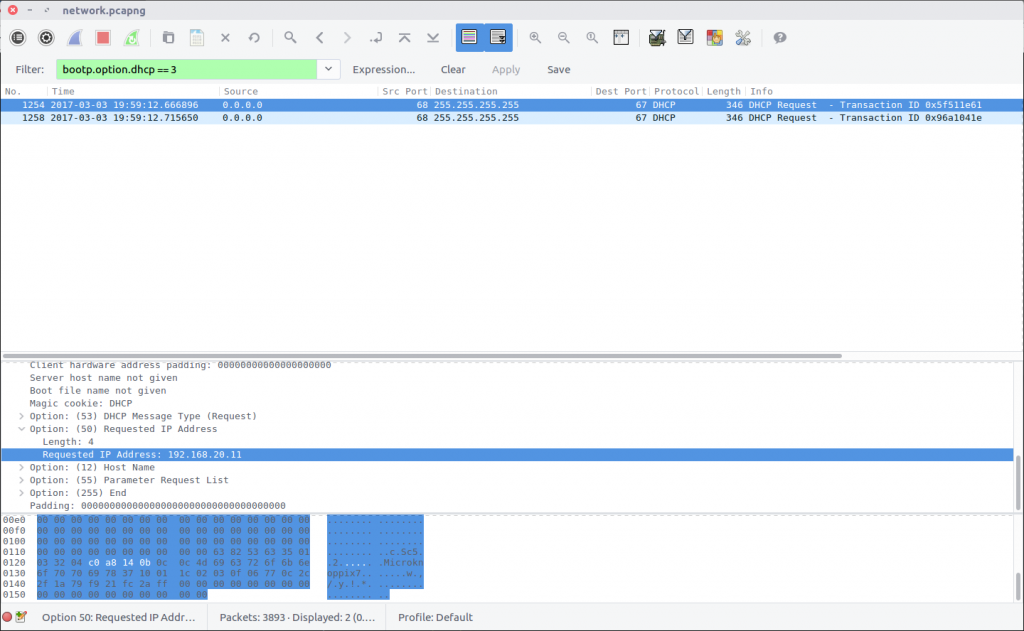
After answering the DHCP questions, we know that we can use the following Display Filter to isolate DHCP Request packets:
bootp.option.dhcp == 3
Examining the packet details we find the Requested IP Address field.
flag<192.168.20.11>
02 – Tick Tock (50 points)
What is the NTP server IPv6 address?
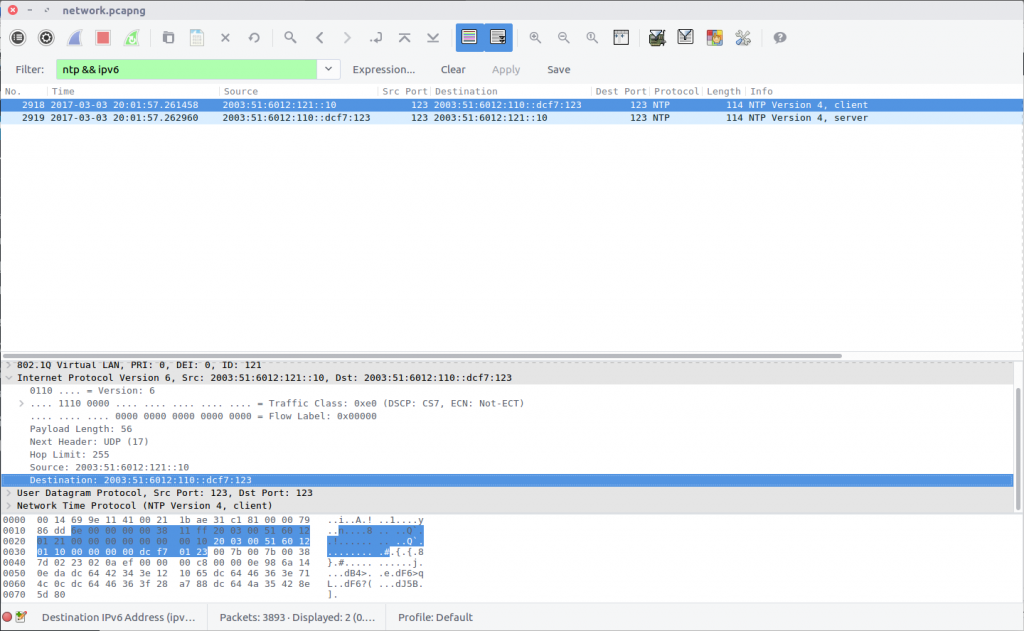
Using a simple Display Filter to isolate NTP traffic using IPv6…
ntp && ipv6
…we can see the IPv6 address of the NTP server.
flag<2003:51:6012:110::dcf7:123>
03 – Who has authority (100 points)
What is the authoritative name server for the domain that is being queried?
Only need one
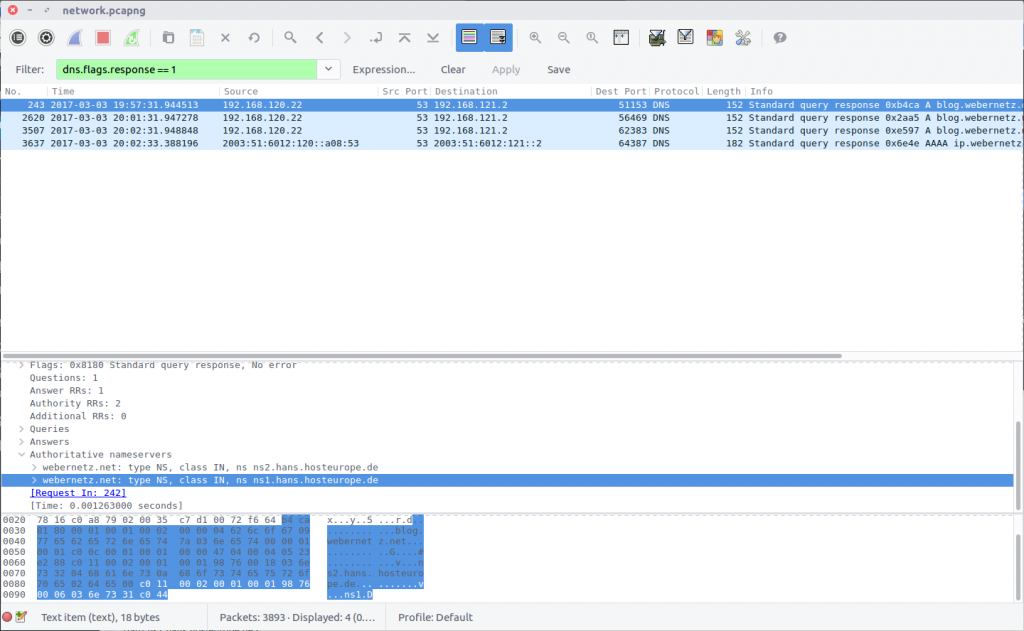
The details of the authoritative name servers can be found in the DNS Response packets. We can filter them out as follows:
dns.flags.response == 1
The Authoritative nameservers field contains the details we are after.
webernetz.net: type NS, class IN, ns ns2.hans.hosteurope.de webernetz.net: type NS, class IN, ns ns1.hans.hosteurope.de
We only need to submit one:
flag<ns1.hans.hosteurope.de>
04 – How am I talking? (150 points)
What is the port for CDP for CCNP-LAB-S2?
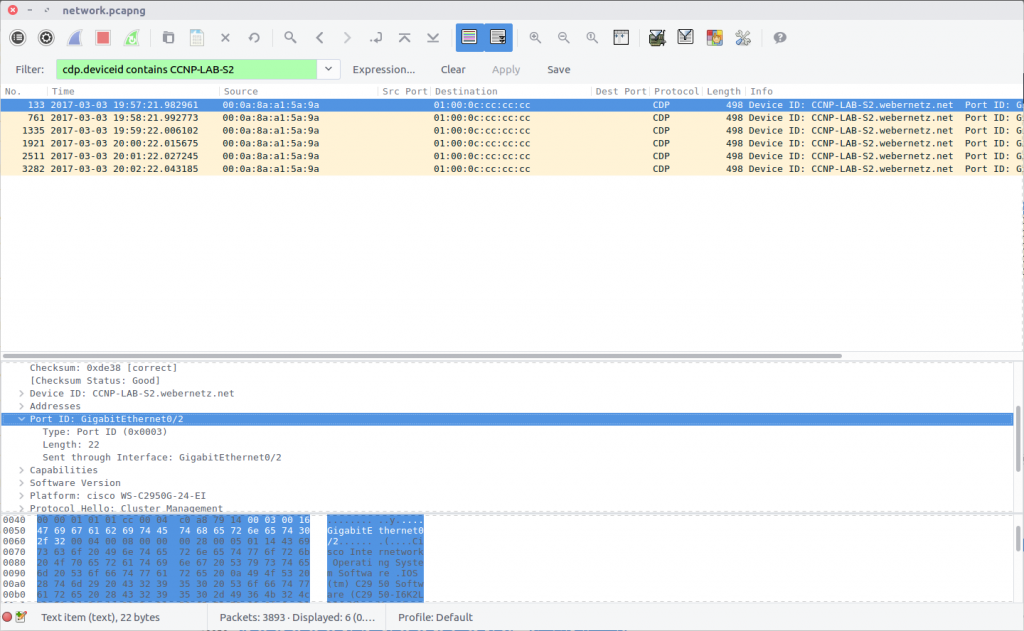
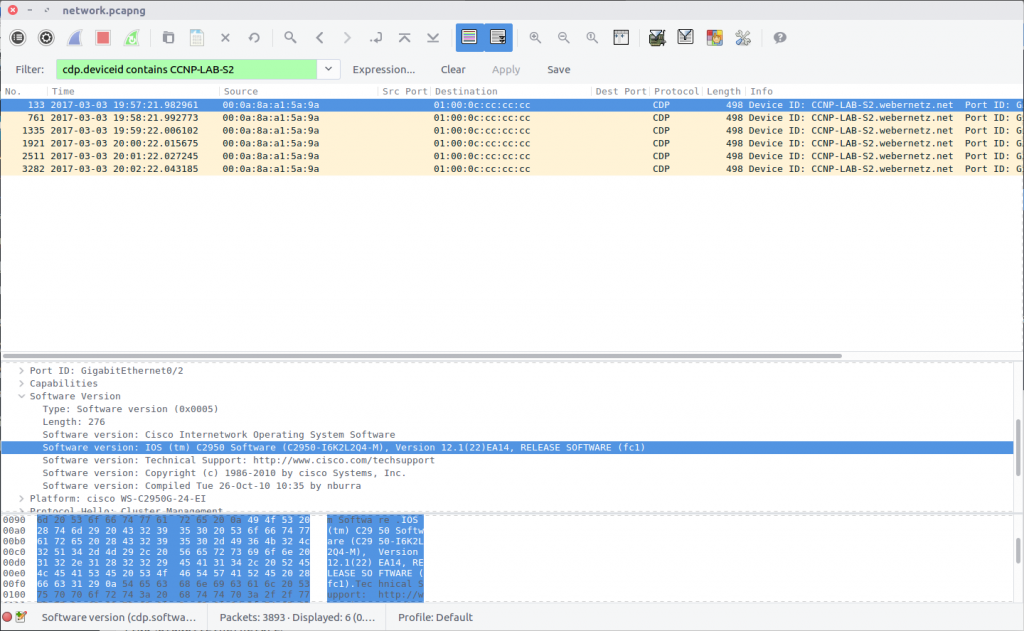
The Cisco Discovery Protocol is used to share information about other directly connected Cisco equipment, such as the operating system version, IP address, and Port ID. The Wireshark wiki has a nice overview of CDP, including a Display Filter reference that we can use to filter out the packets we need based on the Device ID provided in the question.
cdp.deviceid contains CCNP-LAB-S2
Examining the packet we find the Port ID field containing our answer:
flag<GigabitEthernet0/2>
05 – Who changed (150 points)
What is the number of the first VLAN to have a topology change occur?
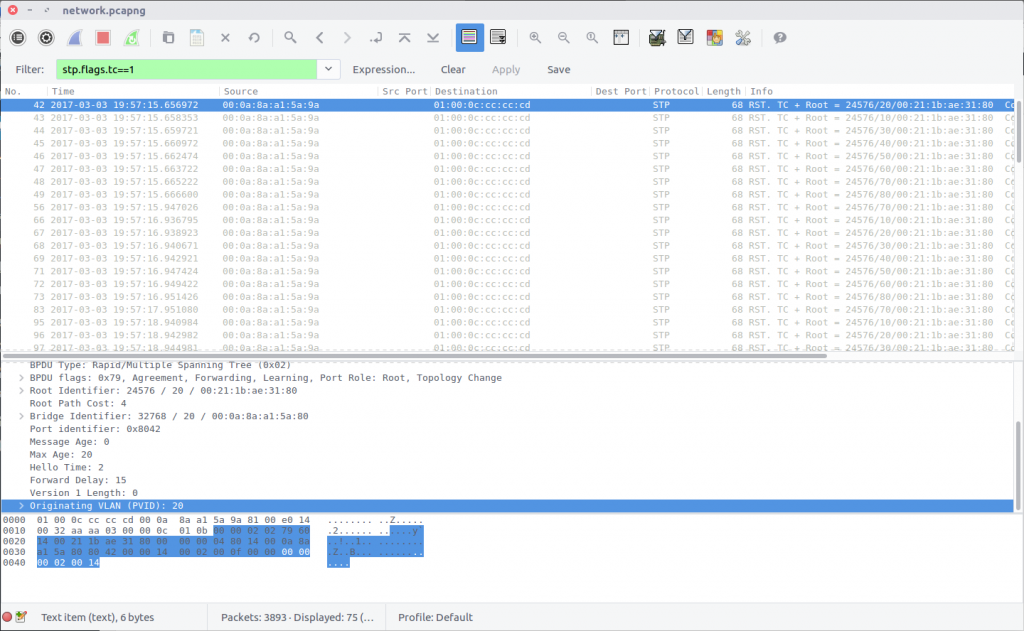
This time we are looking at Spanning Tree Protocol, which I am not familiar with at all! As usual the Wireshark wiki STP page has enough information for us to identify a Display Filter that will isolate Topology Changes (TC).
stp.flags.tc==1
We are looking for the first VLAN to have a Topology Change, so checking the first filtered packet first makes sense. The Originating VLAN field contains the old VLAN ID which is our flag:
flag<20>
06 – How cool are you (200 points)
What is the IOS version running on CCNP-LAB-S2?
We can answer this using the filter from Question 4:
cdp.deviceid contains CCNP-LAB-S2
The Software Version field contains the full version string:
IOS (tm) C2950 Software (C2950-I6K2L2Q4-M), Version 12.1(22)EA14, RELEASE SOFTWARE (fc1)
However the flag only requires the version number itself:
flag<12.1(22)EA14>
07 – Please talk (200 points)
How many Router solicitations were sent?
You only get 3 attempts.
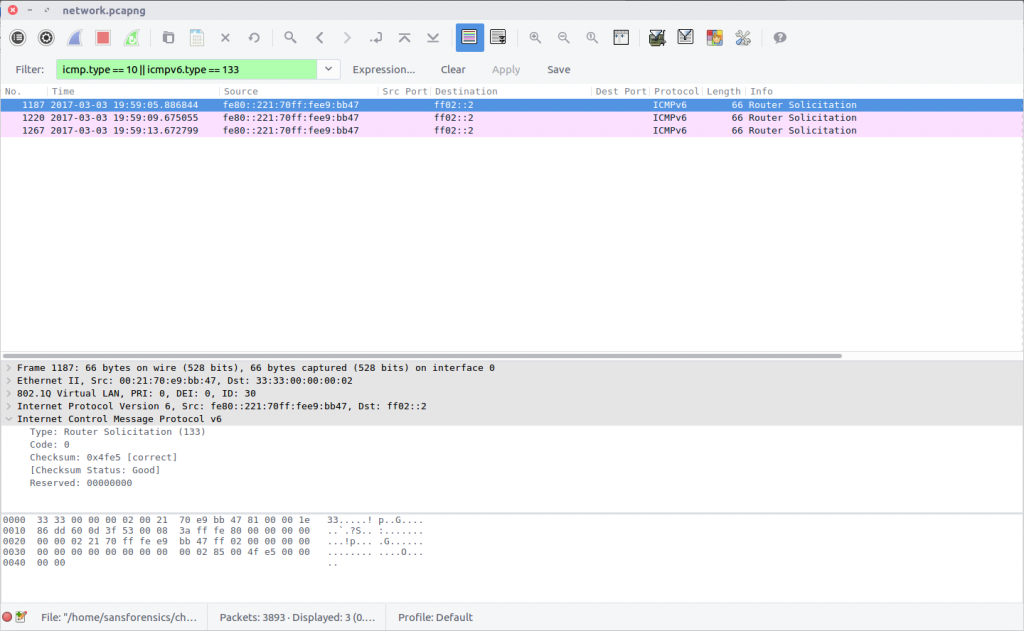
In ICMP, Router Solicitation messages are Type 10; in ICMPv6 they are Type 133. Filter the PCAP to identify both, and count the number of packets returned.
icmpv6.type == 133
flag<3>
08 – Virtual Sharing (200 points)
What is the virtual IP address used for hsrp group 121?
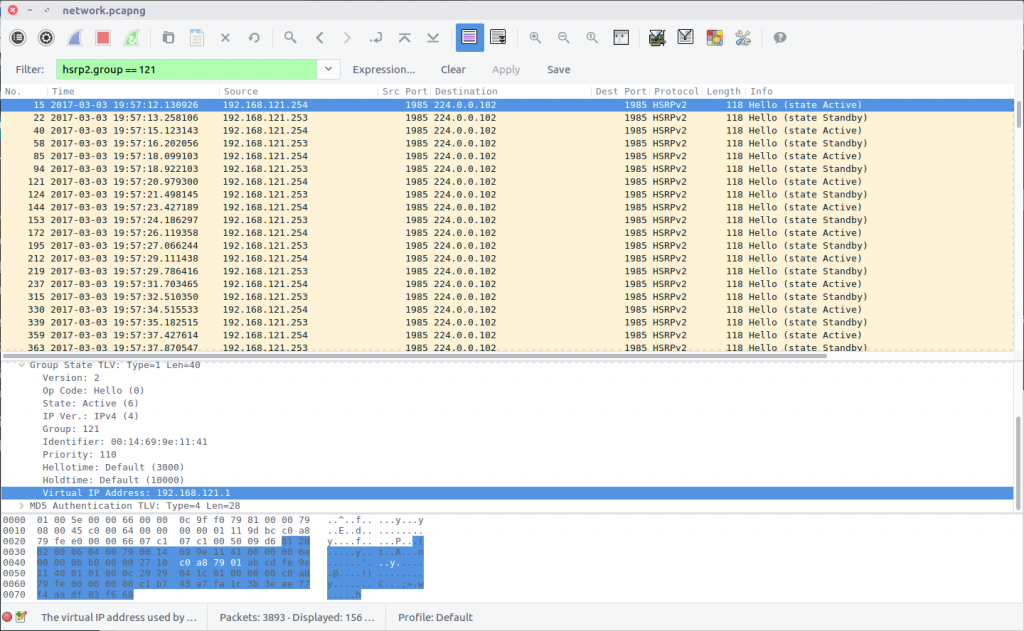
Hot Standby Router Protocol is another Cisco protocol that I am not familiar with. The Wireshark HSRP Display Filter reference proved useful here, specifying a simple filter by group.
hsrp2.group == 121
Examining the first packet returned by the filter, we find the Virtual IP Address field containing our flag:
flag<192.168.121.1>
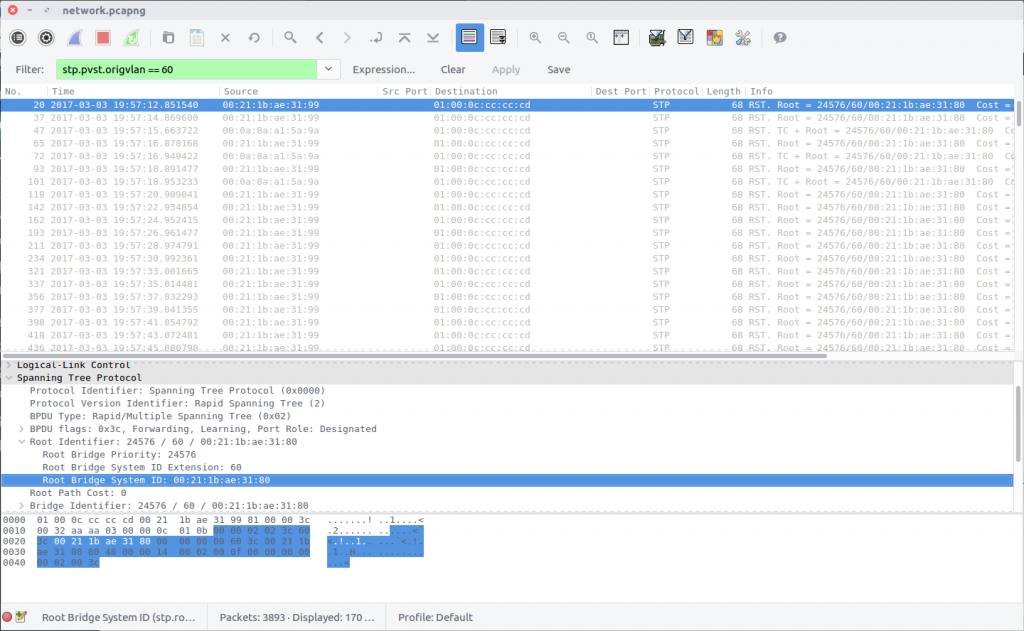
09 – Who is root (200 points)
What is the MAC address for the root bridge for VLAN 60?
Format: flag<XX:XX:XX:XX:XX:XX>
Back to Spanning Tree Protocol for this question. Examining the STP display filter reference again, we find that we can filter the traffic by VLAN ID:
stp.pvst.origvlan == 60
The packet contains a Bridge Identifier field, but what we are after is the MAC address under the Root Identifier field. While writing this I noticed that I left the MAC address in lower-case despite the flag format specifying upper-case; it was still accepted.
flag<00:21:1b:ae:31:80>
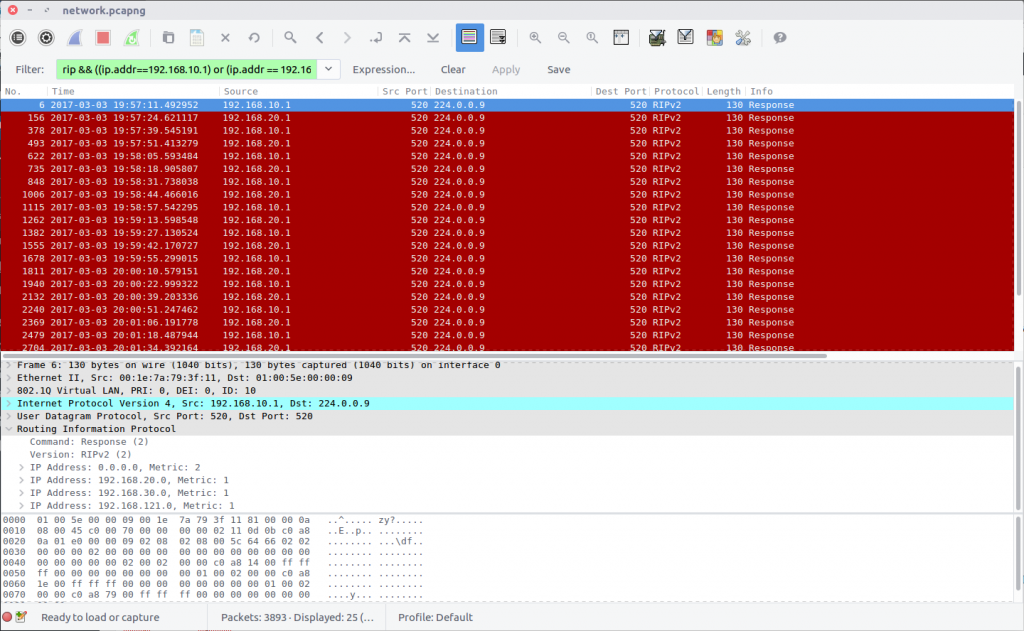
10 – Who is sharing (200 points)
What are the shared networks being advertised by 192.168.10.1 and 192.168.20.1?
If necessary, format lower to higher networks, separated by a semicolon.
This question is related to the Routing Information Protocol, and took a bit of guesswork due to my limited understanding of the protocol. The question specified that we are looking for networks advertised by 192.168.10.1 and 192.168.20.1 so adding those to the Display Filter seemed a sensible starting point.
rip && ((ip.addr==192.168.10.1) or (ip.addr == 192.168.20.1))
Examining the filtered traffic we find that the following networks are advertised:
0.0.0.0/0 192.168.10.0/24 192.168.20.0/24 192.168.30.0/24 192.168.121.0/24
After some trial and error, I ruled out 192.168.10.0/24 and 192.168.20.0/24 as these are the networks our traffic is originating from, and ended up with the following which was accepted as the flag.
flag<0.0.0.0/0;192.168.30.0/24;192.168.121.0/24>
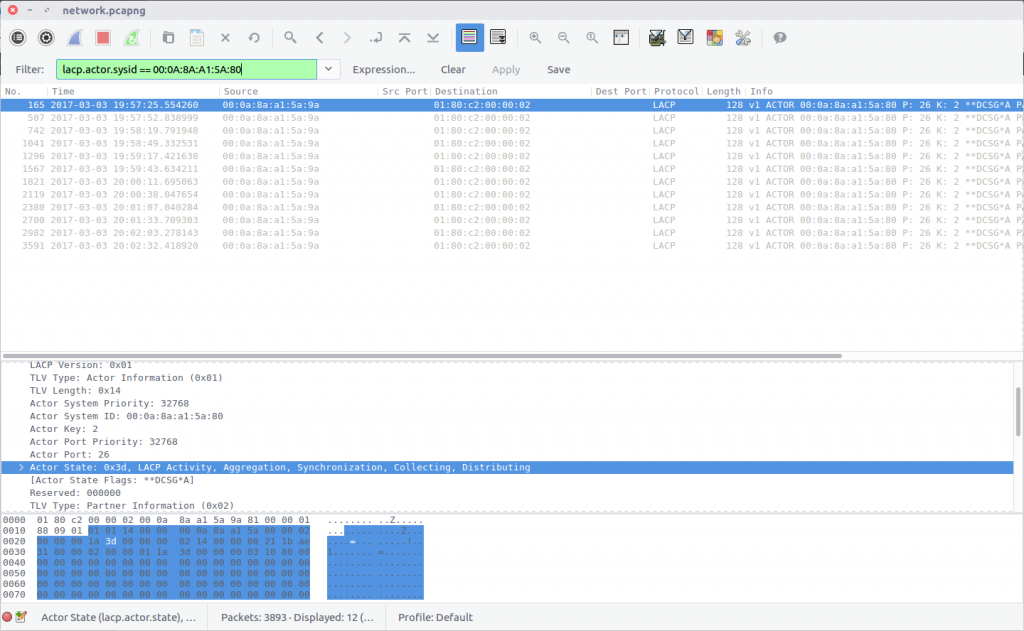
11 – Working together (200 points)
What is the actor state when the actor is “00:0a:8a:a1:5a:80”?
Relying on Google for help, I found that the “actor state” referred to in the question was likely part of the Link Aggregation Control Protocol, and after consulting the LACP display filter reference, I was able to find traffic relating to our specified MAC address:
lacp.actor.sysid == 00:0A:8A:A1:5A:80
Find the Actor State field in the packet and we have our flag:
flag<0x3d>
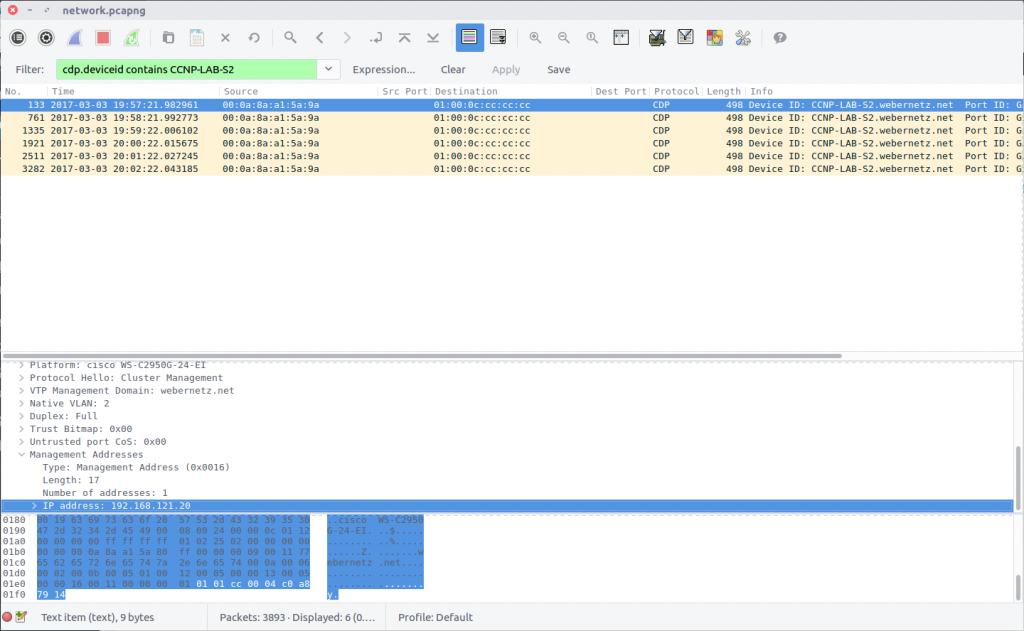
12 – How are you controlled (250 points)
What is the management address of CCNP-LAB-S2?
Once again we are back to Cisco Discovery Protocol, specifically device CCNP-LAB-S2.
cdp.deviceid contains CCNP-LAB-S2
The flag is the IP address listed in the Management Addresses field.
flag<192.168.121.20>
13 – Sharing is caring (250 points)
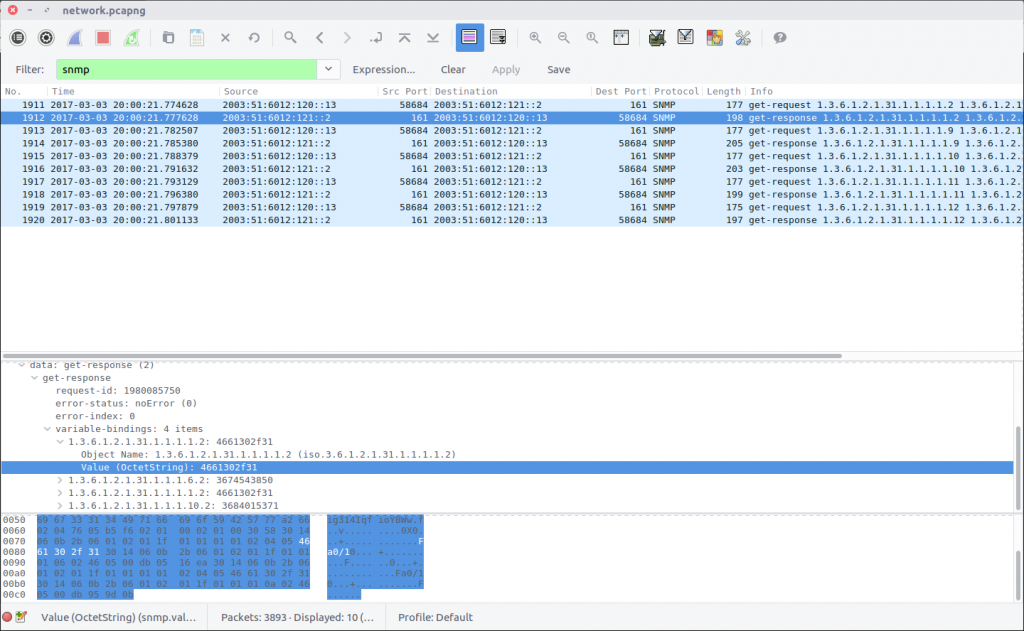
What is the interface being reported on in the first SNMP query?
Simple Network Management Protocol is used to monitor and manage network devices. Queries are made using strings of numbers known as Object IDs (OID) which can be translated into something more easily readable but that wasn’t necessary in this case. We can filter the SNMP traffic and examine the first response packet:
snmp
We can see the result of the query in the first field under the Variable-Bindings section:
1.3.6.1.2.1.31.1.1.1.1.2: 4661302f31
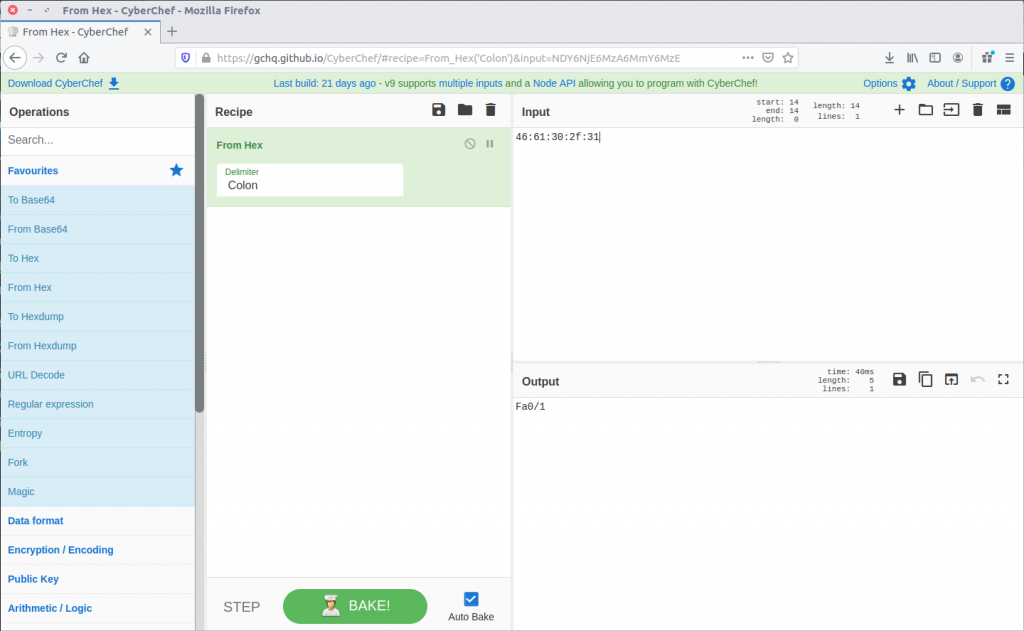
The first part is the OID, and the second is the response. I first tried entering the response as the flag but it was not accepted, leading me to think it was somehow encoded. Time for CyberChef!
A simple From Hex operation and we have something that looks like a network interface identifier. This time, the flag was accepted!
flag<Fa0/1>
14 – Last update (500 points)
When was the NVRAM config last updated?
Format: flag<HH:MM:SS mm/dd/yyyy>
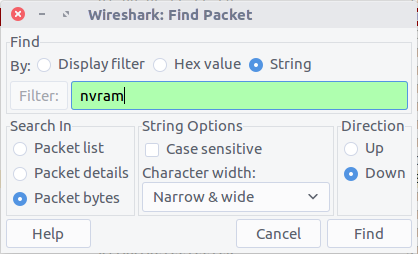
NVRAM is where configuration details for switches, routers, and other network appliances are stored so that they can survive a reboot. I guessed we were looking for a timestamp inside a packet, or for a newly updated device configuration transferred over an unencrypted protocol. As the question does not specify which device received an update, or which protocols might have been used, I opted to use Wireshark’s search function to look for any occurrence of “nvram” in the packet bytes.
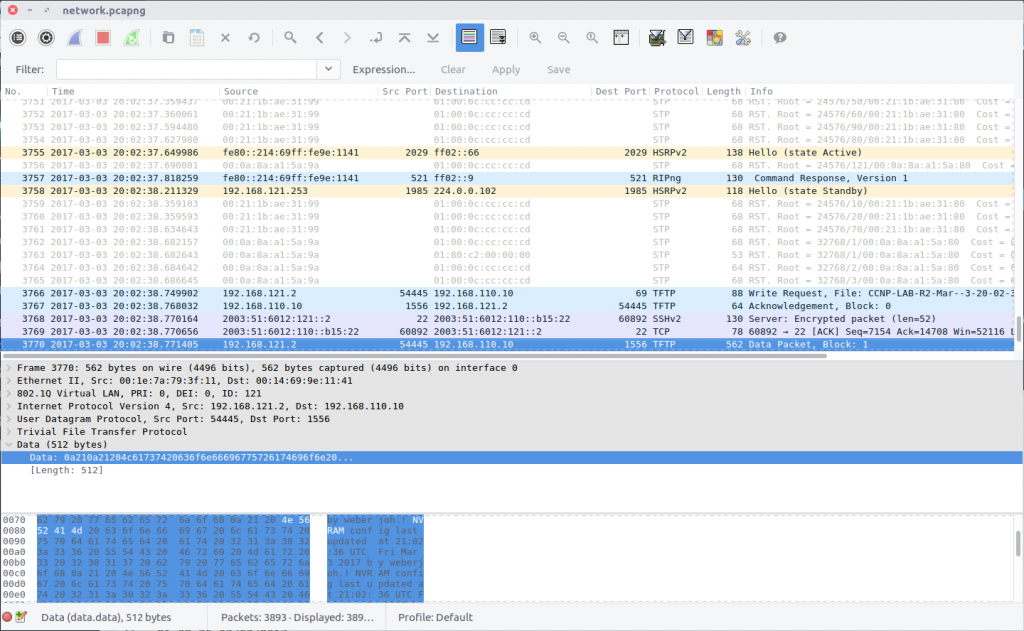
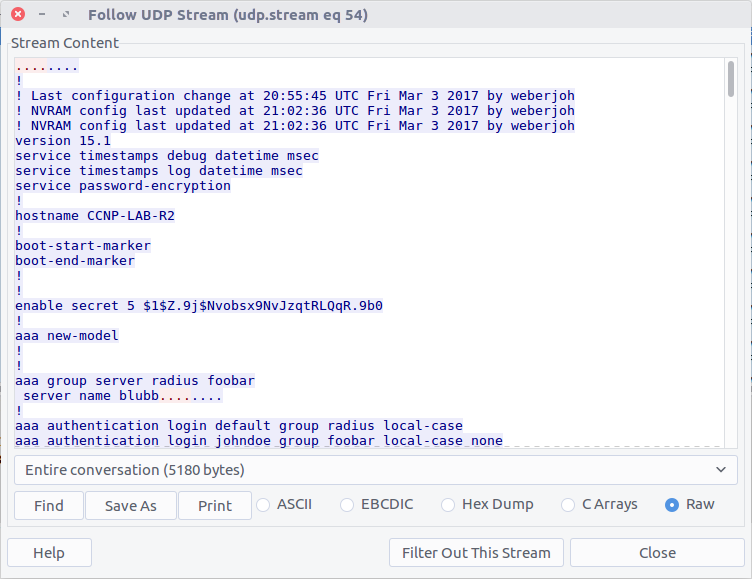
The search finds the first hit in Packet #3770 which is part of a Trivial File Transfer Protocol session; TFTP is often used to modify configuration files on network devices, so this makes sense.
Following the UDP Stream (#54) shows us the content of the configuration file, including the last update time:
! NVRAM config last updated at 21:02:36 UTC Fri Mar 3 2017 by weberjoh
Modify the timestamp to fit the specified format and we have our flag.
flag<21:02:36 03/03/2017>
15 – Some Authentication (500 points)
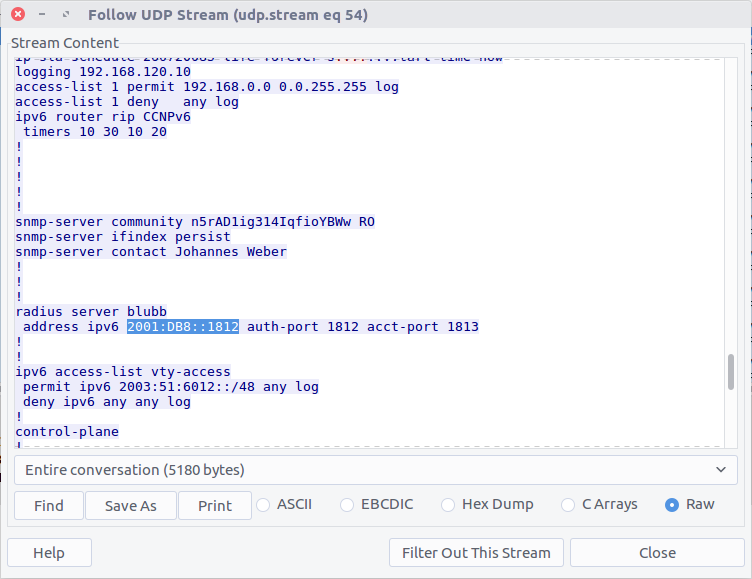
What is the IP of the radius server?
The PCAP file does not contain any RADIUS traffic, but perhaps the configuration file we extracted in Question 14 contains our answer.
There we go!
flag<2001:DB8::1812>
16 – Some more sharing (500 points)
What IPv6 prefixes are being advertised that will be used by clients?
If necessary, format lower to higher networks, separated by a semicolon.
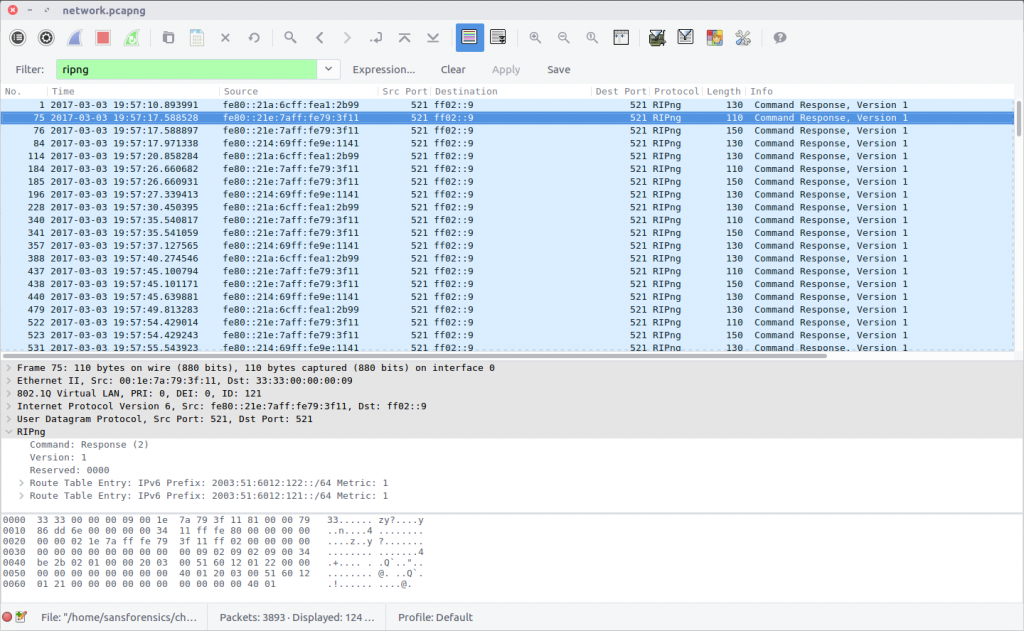
This question is similar to Question 10, but this time we are looking at the RIPng protocol, using the following filter:
ripng
As with Question 10, there are multiple prefixes listed, and I don’t understand the protocol. After some trial and error I found that the following combination was accepted as the correct answer.
flag<2003:51:6012:121::/64;2003:51:6012:122::/64>
4 thoughts on “DFA/CCSC Spring 2020 CTF – Wireshark – network.pcapng Write-up”