In May 2020 the Champlain College Digital Forensics Association, in collaboration with the Champlain Cyber Security Club, released their Spring 2020 DFIR CTF including Windows, MacOS, and Apple iOS images, as well as network traffic analysis, OSINT, and reversing challenges. This series of write-ups covers the network forensics section. As the questions were split over multiple PCAP files (shell, smb, dhcp, network, dns, and https), I have decided to split my write-ups by PCAP for ease of reading.
This write-up covers the questions relating to the smb PCAP file.
MD5: 049cf5868027662393de6e15fd8322de SHA1: af75d7b34e6476e6fc76c6ac3586f153c697ece7
01 – I am groot (50 points)
What is the tree that is being browsed?
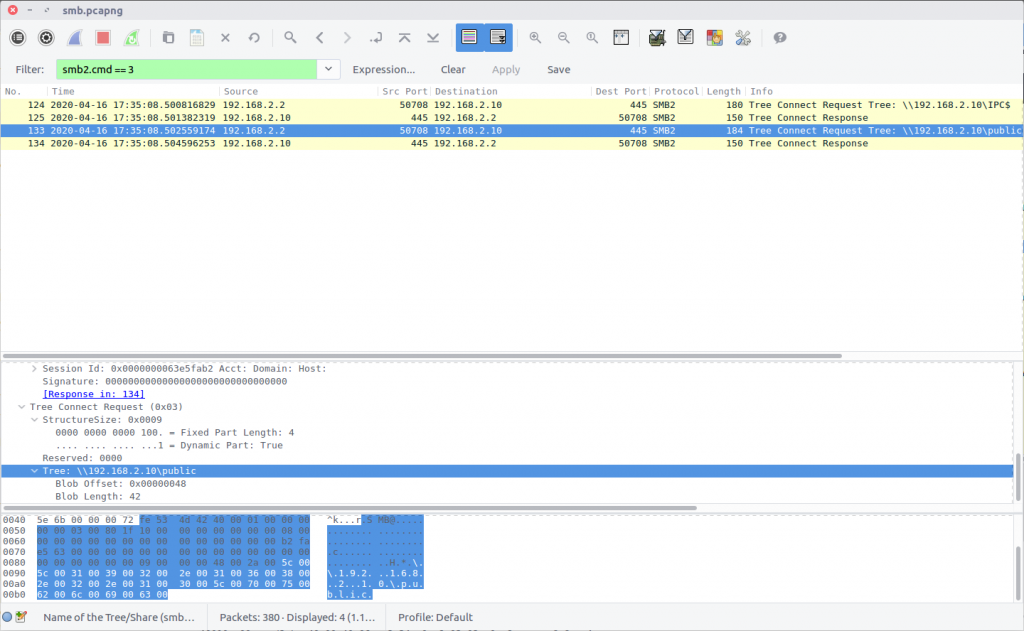
The Wireshark wiki contains a good overview of the SMB2 protocol, including a very helpful list of Opcodes. We can isolate the Tree Connect request packets using the following filter to specify Opcode 0x03:
smb2.cmd == 3
Although there is a Tree Connect request to the IPC$ share in packet 124, the share that ends up being browsed is \public.
flag<\\192.168.2.10\public>
02 – Yellow Brick Road (50 points)
What is the path of the file that is opened?
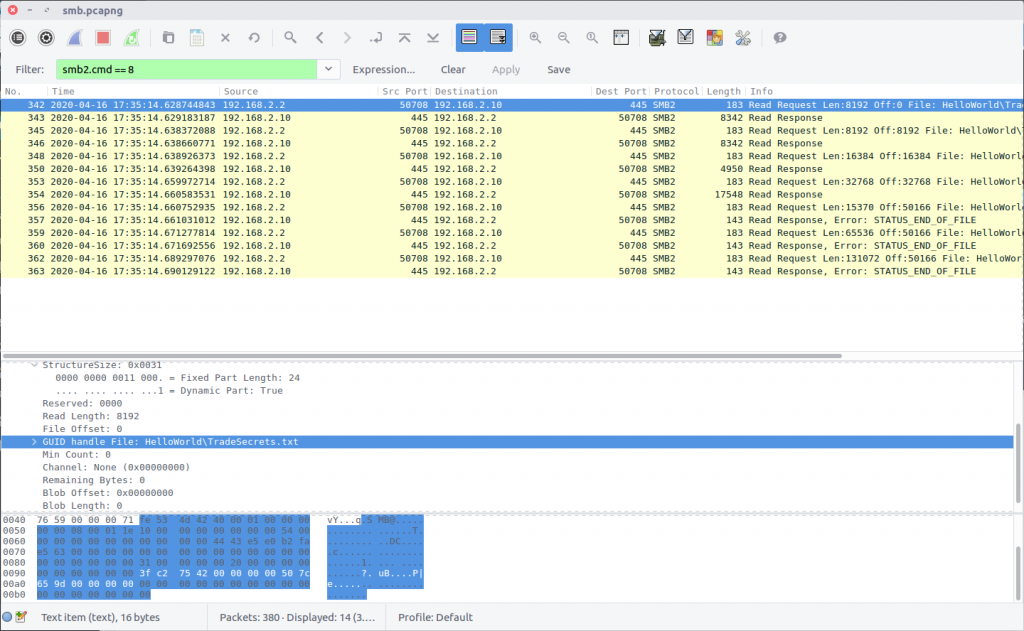
Consulting the list of SMB2 Opcodes, we find that file Read requests are signified by Opcode 0x08, and apply the following filter:
smb2.cmd == 8
Examining the first packet to contain a Read request (Packet 342), we see that the requested file path is HelloWorld\TradeSecrets.txt
flag<HelloWorld\TradeSecrets.txt>
03 – Uh uh uh (75 points)
What is the hex status code when the user SAMBA\jtomato logs in?
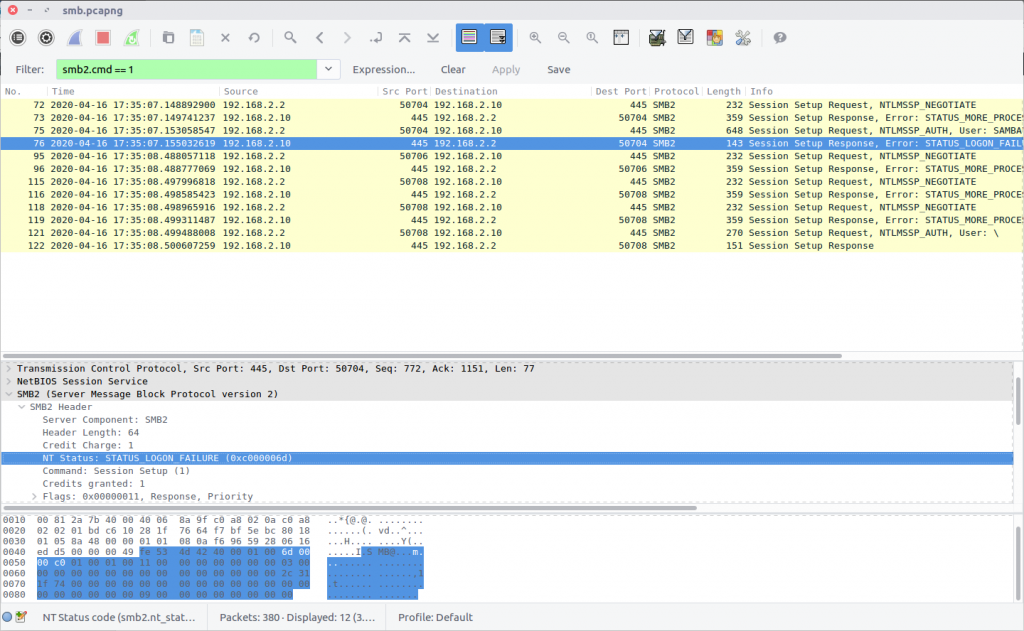
Again, consulting the Wireshark wiki we find that the Session Setup operations are signified by Opcode 0x01; filtered as below:
smb2.cmd == 1
We can see the user SAMBA\jtomato attempt to login in Packet 75. Packet 76 shows the corresponding LOGIN FAILURE, with the hex status code 0xc000006d.
flag<0xc000006d>
04 – According to all known laws of aviation (100 points)
There is a nice simple flag in the file that was accessed.
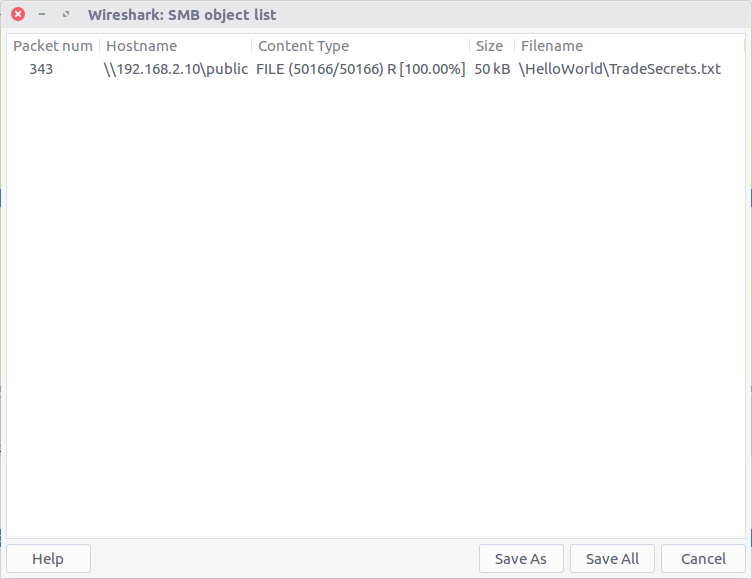
Wireshark allows us to easily export SMB Objects using a graphical interface.
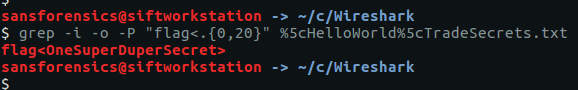
Wireshark has identified the TradeSecrets.txt file referenced in Question 2, allowing us to extract it from the PCAP; now to find the hidden flag, we can use grep. As we know the flag format we have a good starting point, instructing grep to output progressively more characters until the full flag is revealed.
grep -i -o -P "flag<.{0,20}" %5cHelloWorld%5cTradeSecrets.txt
flag<OneSuperDuperSecret>
5 thoughts on “DFA/CCSC Spring 2020 CTF – Wireshark – smb.pcapng Write-up”